Security News
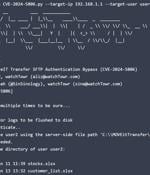
A newly disclosed critical security flaw impacting Progress Software MOVEit Transfer is already seeing exploitation attempts in the wild shortly after details of the bug were publicly disclosed....
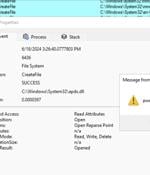
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Highlights Zero-day exploits are vulnerabilities in software or hardware that are unknown to the vendor or developer, so there is no patch or fix available at the time of their discovery. The most infamous cases of zero-day exploits include the MOVEit and Stuxnet vulnerabilities.

The Kraken crypto exchange disclosed today that alleged security researchers exploited a zero-day website bug to steal $3 million in cryptocurrency and then refused to return the funds. The hack was disclosed by Kraken Chief Security Officer Nick Percoco on X, explaining that the exchange's security team received a vague bug report on June 9th about an "Extremely critical" that allowed anyone to increase the balances in a Kraken wallet artificially.

Threat actors are luring unsuspecting users with free or pirated versions of commercial software to deliver a malware loader called Hijack Loader, which then deploys an information stealer known...

If it's actually a "Zero day" then by the definition it's unknown thus not in the LLM "Weights". "Researchers have shown that LLM agents can exploit real-world vulnerabilities when given a description of the vulnerability and toy capture-the-flag problems."

Legitimate-but-compromised websites are being used as a conduit to deliver a Windows backdoor dubbed BadSpace under the guise of fake browser updates. "The threat actor employs a multi-stage...

A proof-of-concept exploit for a critical Veeam Recovery Orchestrator authentication bypass vulnerability tracked as CVE-2024-29855 has been released, elevating the risk of being exploited in attacks. CVE-2024-29855, rated 9.0 as per CVSS v3.1, is an authentication bypass vulnerability impacting Veeam Recovery Orchestrator versions 7.0.0.337 and 7.1.0.205 and older.

State-sponsored threat actors backed by China gained access to 20,000 Fortinet FortiGate systems worldwide by exploiting a known critical security flaw between 2022 and 2023, indicating that the...