Security News

The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The...
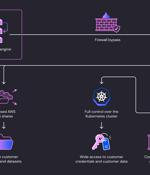
Cybersecurity researchers have uncovered security shortcomings in SAP AI Core cloud-based platform for creating and deploying predictive artificial intelligence workflows that could be exploited to get hold of access tokens and customer data. "The vulnerabilities we found could have allowed attackers to access customers' data and contaminate internal artifacts - spreading to related services and other customers' environments," security researcher Hillai Ben-Sasson said in a report shared with The Hacker News.

CISA and the FBI urged software companies on Wednesday to review their products and eliminate path OS command injection vulnerabilities before shipping. "OS command injection vulnerabilities arise when manufacturers fail to properly validate and sanitize user input when constructing commands to execute on the underlying OS," today's joint advisory explains.

Google has launched kvmCTF, a new vulnerability reward program first announced in October 2023 to improve the security of the Kernel-based Virtual Machine hypervisor that comes with $250,000 bounties for full VM escape exploits. An active and key KVM contributor, Google developed kvmCTF as a collaborative platform to help identify and fix vulnerabilities, bolstering this vital security layer.

Last year alone, over 30,000 new vulnerabilities were published, with a new vulnerability emerging approximately every 17 minutes - averaging 600 new vulnerabilities per week, according to Skybox Security. The report highlights a critical gap in remediation efforts, with the average time to patch exceeding 100 days, contrasted against the finding that 75% of new vulnerabilities are exploited in 19 days or less.

If it's actually a "Zero day" then by the definition it's unknown thus not in the LLM "Weights". "Researchers have shown that LLM agents can exploit real-world vulnerabilities when given a description of the vulnerability and toy capture-the-flag problems."

In this Help Net Security video, Dr. Pedram Hayati, CEO at SecDim, and Fil Filiposki, founder of AttackForge, discuss how the two companies have formed a strategic collaboration to tackle the major challenge of resurfacing vulnerabilities. By integrating SecDim's AppSec Learning wargame into AttackForge, a PenTest management platform, engineers gain a sandbox to explore real-world vulnerabilities safely.

June 2024 Patch Tuesday is here and Microsoft has delivered fixes for a critical MSMQ flaw and a RCE vulnerability in Microsoft Outlook. CVE-2024-30080 is a use after free flaw affecting Microsoft Message Queuing and can be exploited by unauthenticated attackers by sending a specially crafted malicious MSMQ packet to a MSMQ server.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.