Security News
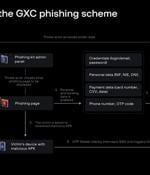
A Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service offerings to the next level. The phishing kit is priced anywhere between $150 and $900 a month, whereas the bundle including the phishing kit and Android malware is available on a subscription basis for about $500 per month.

The seemingly paradoxical solution to these growing threats is further development and research into more sophisticated offensive AI. Plato's adage, "Necessity is the mother of invention," is an apt characterization of cybersecurity today, where new AI-driven threats drive the innovation of more advanced security controls. While developing more sophisticated offensive AI tools and techniques is far from morally commendable, it continues to emerge as an inescapable necessity.

While sysadmins recognize AI's potential, significant gaps in education, cautious organizational adoption, and insufficient AI maturity hinder widespread implementation, leading to mixed results and disruptions in 16% of organizations, according to Action1. "Our findings indicate that, despite some trial and error in AI implementation among sysadmins, organizations generally approach AI cautiously. Implementation projects are predominantly focused on a few IT areas, and even among those that have been implemented, results are mixed. This underscores the fact that AI technology still needs time to mature and evolve before AI-driven solutions become more widespread and practical."

As AI-generated deepfake attacks and identity fraud become more prevalent, companies are developing response plans to address these threats, according to GetApp. Much like phishing attack preparation, it appears that companies are looking to run simulations of attacks to increase preparedness as a majority of respondents work in companies where this is already implemented.

The hybrid multicloud strategies that many Australian enterprises have adopted over the last decade could be made more complex by new AI applications. The only solutions could be rationalisation...

91% of respondents say their security budget is increasing this year, demonstrating a growing recognition of the importance of cybersecurity within organizations, according to Seemplicity. Vendor...

Join Intel, DETASAD, Juniper Networks, and Arqit to hear essential strategies in this webinar on July 30th Webinar Artificial Intelligence (AI) is revolutionizing industries worldwide, but with...

Legacy security measures, while offering a baseline level of protection, heavily rely on predefined signatures and a narrow definition of the “abnormal.” They often follow a reactive approach, can...

Webinar As artificial intelligence continues to transform industries in the Middle East, protecting systems from cyber threats is critical. Industry awareness: Explore the current state of AI awareness across various sectors in the Middle East, and understand specific industry challenges and solutions.

How should CISOs approach AI adoption? When weighing new AI tools, CISOs must examine the risk of a few key factors. These considerations apply to all tools that may leverage AI across all business departments, not just security tools that use AI. The first is data handling practices, from collection and processing to storage and encryption, ensuring robust access controls are in place.