

Can Security Experts Leverage Generative AI Without Prompt Engineering Skills?
A study at Rensselaer Polytechnic Institute presented at ISC2 Security Congress compared...

NordVPN Review (2024): Is NordVPN Worth the Cost?
Is NordVPN worth it? How much does it cost and is it safe to use? Read our NordVPN review to...

No, The Chinese Have Not Broken Modern Encryption Systems with a Quantum Computer
The headline is pretty scary: “China’s Quantum Computer Scientists Crack Military-Grade...


A Comprehensive Guide to Finding Service Accounts in Active Directory
Service accounts are vital in any enterprise, running automated processes like managing...
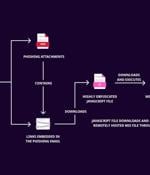
Bumblebee and Latrodectus Malware Return with Sophisticated Phishing Strategies
Two malware families that suffered setbacks in the aftermath of a coordinated law enforcement...

Malicious npm Packages Target Developers' Ethereum Wallets with SSH Backdoor
Cybersecurity researchers have discovered a number of suspicious packages published to the npm...
Vulnerabilities by Risk level (Last 12 months)
Vulnerabilities by Vendor (Last 12 months)
Latest Vulnerabilities
-
CVE-2024-10200
7.5Administrative Management System from Wellchoose has a Path Traversal vulnerability, allowing unauthenticated remote attackers to exploit this vulnerability to download arbitrary files on the server.
-
CVE-2024-10201
8.8Administrative Management System from Wellchoose does not properly validate uploaded file types, allowing remote attackers with regular privileges to upload and execute webshells.
-
CVE-2024-10202
8.8Administrative Management System from Wellchoose has an OS Command Injection vulnerability, allowing remote attackers with regular privileges to inject and execute arbitrary OS commands.
-
CVE-2024-10171 - SQL Injection vulnerability in Code-Projects Blood Bank System 1.0
4.9A vulnerability, which was classified as critical, was found in code-projects Blood Bank System up to 1.0. Affected is an unknown function of the file /admin/massage.php. The manipulation of the...
-
CVE-2024-10170 - SQL Injection vulnerability in Fabianros Hospital Management System 1.0
9.8A vulnerability, which was classified as critical, has been found in code-projects Hospital Management System 1.0. This issue affects some unknown processing of the file get_doctor.php. The...
Latest Critical Vulnerabilities
-
CVE-2024-10170 - SQL Injection vulnerability in Fabianros Hospital Management System 1.0
9.8A vulnerability, which was classified as critical, has been found in code-projects Hospital Management System 1.0. This issue affects some unknown processing of the file get_doctor.php. The...
-
CVE-2024-10165 - SQL Injection vulnerability in Codezips Sales Management System 1.0
9.8A vulnerability was found in Codezips Sales Management System 1.0. It has been declared as critical. Affected by this vulnerability is an unknown functionality of the file deletecustcom.php. The...
-
CVE-2024-10166 - SQL Injection vulnerability in Codezips Sales Management System 1.0
9.8A vulnerability was found in Codezips Sales Management System 1.0. It has been rated as critical. Affected by this issue is some unknown functionality of the file checkuser.php. The manipulation...
-
CVE-2024-10167 - SQL Injection vulnerability in Codezips Sales Management System 1.0
9.8A vulnerability classified as critical has been found in Codezips Sales Management System 1.0. This affects an unknown part of the file deletecustind.php. The manipulation of the argument id leads...
-
CVE-2024-10119
9.8The wireless router WRTM326 from SECOM does not properly validate a specific parameter. An unauthenticated remote attacker could execute arbitrary system commands by sending crafted requests.
-
CVE-2024-10118
9.8SECOM WRTR-304GN-304TW-UPSC does not properly filter user input in the specific functionality. Unauthenticated remote attackers can exploit this vulnerability to inject and execute arbitrary...
-
CVE-2024-43566 - Unspecified vulnerability in Microsoft Edge Chromium
9.8Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
-
CVE-2024-9862
9.8The Miniorange OTP Verification with Firebase plugin for WordPress is vulnerable to Arbitrary User Password Change in versions up to, and including, 3.6.0. This is due to the plugin providing...