Security News
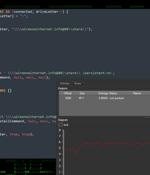
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver malware called SSLoad. The campaign, codenamed FROZEN#SHADOW by Securonix, also...

American telecom provider Frontier Communications is restoring systems after a cybercrime group breached some of its IT systems in a recent cyberattack. Frontier is a leading U.S. communications provider that provides gigabit Internet speeds over a fiber-optic network to millions of consumers and businesses across 25 states.

Microsoft has finally lifted a compatibility hold blocking Windows 10 users from updating to Windows 11 on systems with Intel Smart Sound Technology audio drivers and Intel 11th Gen Core processors. The company first acknowledged in November 2021 that some Intel audio drivers were triggering blue screens back on Windows 11 21H2 devices when it also added safeguard holds blocking Windows 11 upgrades from being offered to customers on affected systems.

Researchers have demonstrated the "First native Spectre v2 exploit" for a new speculative execution side-channel flaw that impacts Linux systems running on many modern Intel processors. Spectre V2 is a new variant of the original Spectre attack discovered by a team of researchers at the VUSec group from VU Amsterdam.

A critical security flaw in the Rust standard library could be exploited to target Windows users and stage command injection attacks. The vulnerability, tracked as CVE-2024-24576, has a CVSS score...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The malicious code inserted into the open-source library XZ Utils, a widely used package present in major Linux distributions, is also capable of facilitating remote code execution, a new analysis...

Rew Appel shepherded a public comment-signed by twenty election cybersecurity experts, including myself-on best practices for ballot marking devices and vote tabulation. Hand-marked and hand-counted ballots remove the uncertainty introduced by use of electronic machinery and the ability of bad actors to exploit electronic vulnerabilities to remotely alter the results.

The Russia-linked threat actor known as Turla infected several systems belonging to an unnamed European non-governmental organization (NGO) in order to deploy a backdoor called TinyTurla-NG. "The...
A new denial-of-service attack dubbed 'Loop DoS' targeting application layer protocols can pair network services into an indefinite communication loop that creates large volumes of traffic. The attack is possible due to a vulnerability, currently tracked as CVE-2024-2169, in the implementation of the UDP protocol, which is susceptible to IP spoofing and does not provide sufficient packet verification.