Security News
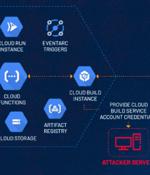
Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform's Cloud Functions service that an attacker could exploit to access other services and sensitive data in an unauthorized manner. "An attacker could escalate their privileges to the Default Cloud Build Service Account and access numerous services such as Cloud Build, storage, artifact registry and container registry," the exposure management company said in a statement.
Using the exploit to abuse a vulnerability that ESET named "EvilVideo," attackers could share malicious Android payloads via Telegram channels, groups, and chats, and make them appear to be multimedia files. "We found the exploit being advertised for sale on an underground forum. In the post, the seller shows screenshots and a video of testing the exploit in a public Telegram channel. We were able to identify the channel in question, with the exploit still available. That allowed us to get our hands on the payload and test it ourselves," explains ESET researcher Lukáš Štefanko, who discovered the Telegram exploit.

Cisco just dropped a patch for a maximum-severity vulnerability that allows attackers to change the password of any user, including admins. Tracked as CVE-2024-20419, the bug carries a maximum 10/10 CVSS 3.1 rating and affects the authentication system of Cisco Smart Software Manager On-Prem.

Grype is an open-source vulnerability scanner designed for container images and filesystems that seamlessly integrates with Syft, a powerful Software Bill of Materials tool. Find vulnerabilities for major operating system packages Find vulnerabilities for language-specific packages Ruby Java JavaScript Python Dotnet Golang PHP Rust.

Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server that could lead to remote code execution attacks. It has been described as a remote command execution flaw in the Gremlin graph traversal language API. "Users are recommended to upgrade to version 1.3.0 with Java11 and enable the Auth system, which fixes the issue," the Apache Software Foundation noted in late April 2024.

Exclusive A Microsoft zero-day exploit that Trend Micro's Zero Day Initiative team claims it found and reported to Redmond in May was disclosed and patched by the Windows giant in July's Patch Tuesday - but without any credit given to ZDI. The flaw, tracked as CVE-2024-38112, is in MSHTML - Microsoft's proprietary browser engine for Internet Explorer. This entire series of unfortunate events not only highlights problems with Microsoft's bug reporting program, but also the coordinated vulnerability disclosure process in general, according to Childs.

The maintainers of the Exim mail transfer agent have fixed a critical vulnerability that currently affects around 1.5 million public-facing servers and can help attackers deliver malware to users. CVE-2024-39929 affects Exim releases up to and including 4.97.1, and has been fixed in Exim v4.98, which was released last week.

A critical security issue has been disclosed in the Exim mail transfer agent that could enable threat actors to deliver malicious attachments to target users' inboxes. "Exim through 4.97.1 misparses a multiline RFC 2231 header filename, and thus remote attackers can bypass a $mime filename extension-blocking protection mechanism, and potentially deliver executable attachments to the mailboxes of end users," according to a description shared on the U.S. National Vulnerability Database.

A BlastRADIUS attack involves the attacker intercepting network traffic between a client, such as a router, and the RADIUS server. While MD5 is well-known to have weaknesses that allow attackers to generate collisions or reverse the hash, the researchers say that the BlastRADIUS attack "Is more complex than simply applying an old MD5 collision attack" and more advanced in terms of speed and scale.
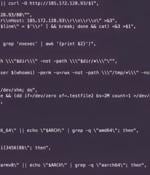
The vulnerability in question is CVE-2024-4577, which allows an attacker to remotely execute malicious commands on Windows systems using Chinese and Japanese language locales. The disclosure comes as Cloudflare said it recorded a 20% year-over-year increase in DDoS attacks in the second quarter of 2024, and that it mitigated 8.5 million DDoS attacks during the first six months.