Security News

Coupled with an exploding ecosystem of third-party apps, endpoint management tools that aren't really designed to handle patch management, bandwidth issues, and architectural challenges, IT teams have "An overwhelming amount of work to do," Hewitt told us. Endpoint management biz Adaptiva revealed in its 2023 state of patch handling report [PDF] that the average organization manages around 2,900 software applications, and 69 percent of IT teams believe it's impossible to get all of them patched on schedule.
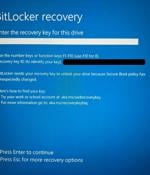
Not now, Microsoft Some Windows devices are presenting users with a BitLocker recovery screen upon reboot following the installation of July's Patch Tuesday update.…

Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server that could lead to remote code execution attacks. It has been described as a remote command execution flaw in the Gremlin graph traversal language API. "Users are recommended to upgrade to version 1.3.0 with Java11 and enable the Auth system, which fixes the issue," the Apache Software Foundation noted in late April 2024.

Netgear warned customers to update their devices to the latest available firmware, which patches stored cross-site scripting and authentication bypass vulnerabilities in several WiFi 6 router models. The stored XSS security flaw impacts the XR1000 Nighthawk gaming router.

Another new ransomware gang, this one dubbed EstateRansomware, is exploiting a Veeam vulnerability that was patched more than a year ago to drop file-encrypting malware, a LockBit variant, and extort payments from victims. Veeam fixed the flaw, tracked as CVE-2023-27532, in March 2023 for versions 12/11a and later of its backup and replication software.

Patch Tuesday Clear your Microsoft system administrator's diary: The bundle of fixes in Redmond's July Patch Tuesday is a doozy, with at least two bugs under active exploitation. The first of two vulnerabilities for sure under active exploit - CVE-2024-38080 - is a Windows Hyper-V elevation of privilege flaw with a 7.8-out-of-10 CVSS rating, which Microsoft deemed "Important."

Today is Microsoft's July 2024 Patch Tuesday, which includes security updates for 142 flaws, including two actively exploited and two publicly disclosed zero-days. [...]

Microsoft temporarily pulled and then re-released the Windows 11 preview update KB5039302, originally released on June 25th. The original preview was causing reboots on systems using virtualization, such as Azure Virtual Desktop and VMware. Per the announcement, all Kaspersky products must be removed by September 29th. Just as a reminder, last month Microsoft released the final updates for Windows 10 21H2 Education and Enterprise editions.

GitLab has released security updates to address 14 security flaws, including one critical vulnerability that could be exploited to run continuous integration and continuous deployment (CI/CD)...
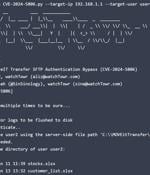
A newly disclosed critical security flaw impacting Progress Software MOVEit Transfer is already seeing exploitation attempts in the wild shortly after details of the bug were publicly disclosed....