Security News

Coupled with an exploding ecosystem of third-party apps, endpoint management tools that aren't really designed to handle patch management, bandwidth issues, and architectural challenges, IT teams have "An overwhelming amount of work to do," Hewitt told us. Endpoint management biz Adaptiva revealed in its 2023 state of patch handling report [PDF] that the average organization manages around 2,900 software applications, and 69 percent of IT teams believe it's impossible to get all of them patched on schedule.

Infisical is an open-source secret management platform developers use to centralize application configurations and secrets, such as API keys and database credentials, while also managing their...

An effective third-party risk management framework ensures that an organization is not derailed by vendor risks and vulnerabilities. Right after you categorize your third-party vendors based on their importance to your organization, next you must define the scope of your third-party risk management services and framework by identification of the type of third parties involved and the risk factors posed by them.

For either case, you can now develop information security skills with the help of The CISSP Security & Risk Management Training Bundle for just $29.97 through July 21. CISSP: Security & Risk Management covers the security concepts that provide the foundation for all of the other domains.

Portainer Community Edition is an open-source, lightweight service delivery platform for containerized applications. "I created Portainer, initially for my own needs. Back in 2016 I was operating a Public Cloud provider in Asia, and wanted to offer a Container as a Service solution to market. At the time, that meant Docker. There were no Cloud Provider management UI's for Docker then, so I created Portainer to act as such. In a way, Portainer enabled a domestic market version of AWS ECS before ECS was popular. However, Portainer quickly took on a life of its own. I open-sourced the UI, which was"discovered" and blogged about, and it took off.

Across various tasks, from predictive analytics to code generation, organizations in all sectors are exploring how AI can add value and increase efficiency. In this Help Net Security video, Ryan Booz, PostgreSQL Advocate at Redgate, discusses the key findings of Redgate's State of the Database Landscape Report.
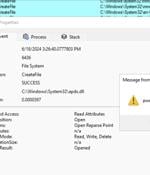
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management...

Qualys CyberSecurity Asset Management 3.0 consolidates asset discovery and risk assessment into a single solution. A key differentiator of Qualys CyberSecurity Asset Management 3.0 is in the way its External Attack Surface Management technology works.

The Tor Project has released Tor Browser 13.5, bringing several improvements and enhancements for Android and desktop versions. The Tor Browser is a specialized open-source web browser designed for anonymous browsing by routing the user's traffic through thousands of volunteer-run servers called nodes/relays, which constitute the Tor network.

As we integrate AI more deeply into vulnerability management processes, organizations can expect enhanced security postures and a shift towards a more proactive and predictive approach to handling cybersecurity threats. AI has some major limitations and even security concerns, especially regarding vulnerability management.