Security News

The Tor Project officially introduced WebTunnel, a new bridge type specifically designed to help bypass censorship targeting the Tor network by hiding connections in plain sight. Tor bridges are relays not listed in the public Tor directory that keep the users' connections to the network hidden from oppressive regimes.

Tails is a portable operating system that protects against surveillance and censorship. Tails can be installed on any USB stick with a minimum of 8 GB. Tails works on most computers under ten years old.

The Tor Project has explained its recent decision to remove multiple network relays that represented a threat to the safety and security of all Tor network users. Tor network relays are routing points that help anonymize the original traffic source through the Tor network by receiving and passing on encrypted data to the next node.

Recent versions of the TorBrowser, specifically because of the updated tor. Microsoft stated, "We've reviewed the submitted files and have determined that they do not fit our definitions of malware or unwanted applications. As such, we've removed the detection."

No miners were involved in this story Tor, which stands for The Onion Router, weathered a massive distributed denial-of-service (DDoS) storm from June last year through to May.…

The overarching mission of the US-based non-profit organization the Tor Project is to advance human rights and make open-source, privacy preserving software available to people globally, so that they can browse the internet privately, protect themselves against surveillance and bypass online censorship. To infosec professionals The Tor Project doesn't need an introduction, but there's always other people out there who have never heard of it.

Clipboard-injector malware disguised as Tor browser installers has been used to steal about $400,000 in cryptocurrency from nearly 16,000 users worldwide so far in 2023, according to Kaspersky researchers. "The Tor Project called to help keep Russian users connected to Tor to circumvent censorship," Vitaly Kamluk, head of Kaspersky's Global Research and Analysis Team for APAC, wrote in a blog about the clipper malware.
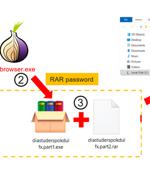
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022. "Clipboard injectors can be silent for years, show no network activity or any other signs of presence until the disastrous day when they replace a crypto wallet address," Vitaly Kamluk, director of global research and analysis team for APAC at Kaspersky, said.

A surge of trojanized Tor Browser installers targets Russians and Eastern Europeans with clipboard-hijacking malware that steals infected users' cryptocurrency transactions. While these malicious Tor installers target countries worldwide, Kaspersky says that most are targeting Russia and Eastern Europe.

Tor Project's Executive Director Isabela Dias Fernandes revealed on Tuesday that a wave of distributed denial-of-service attacks has been targeting the network since at least July 2022. "We have been working hard to mitigate the impacts and defend the network from these attacks. The methods and targets of these attacks have changed over time and we are adapting as these attacks continue."