Security News
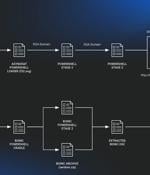
The JavaScript downloader malware known as SocGholish is being used to deliver a remote access trojan called AsyncRAT as well as a legitimate open-source project called BOINC. BOINC, short for Berkeley Open Infrastructure Network Computing Client, is an open-source "Volunteer computing" platform maintained by the University of California with an aim to carry out "Large-scale distributed high-throughput computing" using participating home computers on which the app is installed. The JavaScript downloader, in this case, activates two disjointed chains, one that leads to the deployment of a fileless variant of AsyncRAT and the other resulting in the BOINC installation.

Cybersecurity firm CrowdStrike, which is facing the heat for causing worldwide IT disruptions by pushing out a flawed update to Windows devices, is now warning that threat actors are exploiting the situation to distribute Remcos RAT to its customers in Latin America under the guise of a providing a hotfix. The attack chains involve distributing a ZIP archive file named "Crowdstrike-hotfix.zip," which contains a malware loader named Hijack Loader that, in turn, launches the Remcos RAT payload. Specifically, the archive file also includes a text file with Spanish-language instructions that urges targets to run an executable file to recover from the issue.

An advanced persistent threat group called Void Banshee has been observed exploiting a recently disclosed security flaw in the Microsoft MHTML browser engine as a zero-day to deliver an information stealer called Atlantida. "Variations of the Atlantida campaign have been highly active throughout 2024 and have evolved to use CVE-2024-38112 as part of Void Banshee infection chains," security researchers Peter Girnus and Aliakbar Zahravi said.

Threat actors are quick to weaponize available proof-of-concept (PoC) exploits in actual attacks, sometimes as quickly as 22 minutes after exploits are made publicly available. [...]

Cybersecurity researchers have shed light on a short-lived DarkGate malware campaign that leveraged Samba file shares to initiate the infections. Palo Alto Networks Unit 42 said the activity spanned the months of March and April 2024, with the infection chains using servers running public-facing Samba file shares hosting Visual Basic Script and JavaScript files.

Chinese state-sponsored cyber group APT40 is amazingly fast at adapting public proof-of-concept exploits for vulnerabilities in widely used software, an advisory released by intelligence and cybersecurity agencies from eight countries warns. APT 40 "Appears to prefer exploiting vulnerable, public-facing infrastructure over techniques that require user interaction, such as phishing campaigns," and has been known to exploit vulnerabilities in software such as Log4J, Atlassian Confluence and Microsoft Exchange.

Cybersecurity agencies from Australia, Canada, Germany, Japan, New Zealand, South Korea, the U.K., and the U.S. have released a joint advisory about a China-linked cyber espionage group called APT40, warning about its ability to co-opt exploits for newly disclosed security flaws within hours or days of public release. "APT 40 has previously targeted organizations in various countries, including Australia and the United States," the agencies said.

Hackers are exploiting a critical vulnerability that affects all D-Link DIR-859 WiFi routers to collect account information from the device, including passwords. Although D-Link DIR-859 WiFi router model reached end-of-life and no longer receives any updates, the vendor still released a security advisory explaining that the flaw exists in the "Fatlady.php" file of the device, affects all firmware versions, and allows attackers to leak session data, achieve privilege escalation, and gain full control via the admin panel.

Security researchers have shed more light on the cryptocurrency mining operation conducted by the 8220 Gang by exploiting known security flaws in the Oracle WebLogic Server. "The threat actor...

A group of security researchers from the Graz University of Technology have demonstrated a new side-channel attack known as SnailLoad that could be used to remotely infer a user's web activity....