Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

LastPass is warning of a malicious campaign targeting its users with the CryptoChameleon phishing kit that is associated with cryptocurrency theft. According to researchers at mobile security company Lookout, campaigns using this phishing kit also targeted cryptocurrency platforms Binance, Coinbase, Kraken, and Gemini, using pages that impersonated Okta, Gmail, iCloud, Outlook, Twitter, Yahoo, and AOL. During its investigations, LastPass discovered that its service was recently added to the CryptoChameleon kit, and a phishing site was hosted at at the "Help-lastpass[.]com" domain.

A new phishing campaign has set its eyes on the Latin American region to deliver malicious payloads to Windows systems. "The phishing email contained a ZIP file attachment that when extracted...

Browser fingerprinting is one of many tactics phishing site authors use to evade security checks and lengthen the lifespan of malicious campaigns. While browser fingerprinting has been used by legitimate organizations to uniquely identify web browsers for nearly 15 years, it is now also commonly exploited by cybercriminals: a recent study shows one in four phishing sites using some form of this technique.
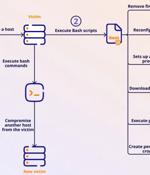
Several malicious Android apps that turn mobile devices running the operating system into residential proxies (RESIPs) for other threat actors have been observed on the Google Play Store. The...

Of these compromised identity records, one in four contained information about the user's network or physical location, putting the individual's identity, platforms they have access to, and physical well-being at risk. Taking a deeper look into how stolen data empowers bad actors to perpetrate cybercrimes including account takeover, fraud, and ransomware, researchers analyzed the exposures of the average digital identity being traded in the criminal underground and found that the average identity appears in as many as nine breaches and is associated with 15 breach records.

The U.S. Department of Justice has charged global cryptocurrency exchange KuCoin and two of its founders for failing to adhere to anti-money laundering requirements, allowing threat actors to use the platform to launder money. Founded in 2017 by Chinese citizens Chun Gan and Ke Tang, KuCoin is one of the largest cryptocurrency exchange platforms to buy, sell, trade, and store a variety of digital currencies.

Developed by OpenAI, ChatGPT has garnered attention across industries for its ability to generate relevant responses to various queries. As the adoption of ChatGPT accelerates, so do discussions surrounding its ethical and security implications.

Application programming interfaces (APIs) are the connective tissue behind digital modernization, helping applications and databases exchange data more effectively. The State of API Security in...

The rise of advanced persistent threats, phishing-as-a-service, ransomware-as-a-service models, and nation-state-sponsored cyber-attacks further compounds the complexity of the threat landscape. It's crucial for enterprises to adapt swiftly, implementing threat intelligence programs to expedite vulnerability remediation and the deployment of suitable security controls tailored to the dynamic threat environment evolution.