Security News

The U.S. Department of Justice on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly carrying out ransomware attacks against healthcare facilities in the country and funneling the payments to orchestrate additional intrusions into defense, technology, and government entities across the world. "Rim Jong Hyok and his co-conspirators deployed ransomware to extort U.S. hospitals and health care companies, then laundered the proceeds to help fund North Korea's illicit activities," said Paul Abbate, deputy director of the Federal Bureau of Investigation.

The U.S. State Department is offering a reward of up to $10 million for information that could lead to the identification or location of a North Korean military hacker identified as Rim Jong Hyok. Part of the Andariel North Korean hacking group, Hyok and other Andariel operatives were linked to Maui ransomware attacks targeting critical infrastructure and healthcare organizations across the United States.

A North Korea-linked threat actor known for its cyber espionage operations has gradually expanded into financially-motivated attacks that involve the deployment of ransomware, setting it apart from other nation-state hacking groups linked to the country. "APT45 is a long-running, moderately sophisticated North Korean cyber operator that has carried out espionage campaigns as early as 2009," researchers Taylor Long, Jeff Johnson, Alice Revelli, Fred Plan, and Michael Barnhart said.

American cybersecurity company KnowBe4 says a person it recently hired as a Principal Software Engineer turned out to be a North Korean state actor who attempted to install information-stealing on its devices. Before hiring the threat actor, KnowBe4 performed background checks, verified the provided references, and conducted four video interviews to ensure they were a real person and that his face matched the one on his CV. However, it was later determined that the person had submitted a U.S. person's stolen identity to dodge the preliminary checks, and also used AI tools to create a profile picture and match that face during the video conference calls.
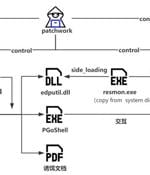
The threat actor known as Patchwork has been linked to a cyber attack targeting entities with ties to Bhutan to deliver the Brute Ratel C4 framework and an updated version of a backdoor called...

The entire database for the notorious BreachForums v1 hacking forum was released on Telegram Tuesday night, exposing a treasure trove of data, including members' information, private messages,...

The Chinese hacking group tracked as 'Evasive Panda' was spotted using new versions of the Macma backdoor and the Nightdoor Windows malware. [...]

Organizations in Taiwan and a U.S. non-governmental organization based in China have been targeted by a Beijing-affiliated state-sponsored hacking group called Daggerfly using an upgraded set of malware tools. Daggerfly, also known by the names Bronze Highland and Evasive Panda, was previously observed using the MgBot modular malware framework in connection with an intelligence-gathering mission aimed at telecom service providers in Africa.

A Latin America-based financially motivated actor codenamed FLUXROOT has been observed leveraging Google Cloud serverless projects to orchestrate credential phishing activity, highlighting the abuse of the cloud computing model for malicious purposes. The campaign involved the use of Google Cloud container URLs to host credential phishing pages with the aim of harvesting login information associated with Mercado Pago, an online payments platform popular in the LATAM region.

UK police have arrested a 17-year-old boy suspected of being involved in the 2023 MGM Resorts ransomware attack and a member of the Scattered Spider hacking collective. "We're proud to have assisted law enforcement in locating and arresting one of the alleged criminals responsible for the cyber attack against MGM Resorts and many others," MGM said as part of the law enforcement statement.