Security News
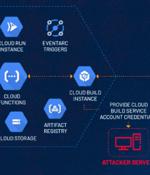
Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform's Cloud Functions service that an attacker could exploit to access other services and sensitive data in an unauthorized manner. "An attacker could escalate their privileges to the Default Cloud Build Service Account and access numerous services such as Cloud Build, storage, artifact registry and container registry," the exposure management company said in a statement.

In this Help Net Security interview, Ava Chawla, Head of Cloud Security at AlgoSec, discusses the most significant cloud security threats CISOs must be aware of in 2024. These threats include data...

A Latin America-based financially motivated actor codenamed FLUXROOT has been observed leveraging Google Cloud serverless projects to orchestrate credential phishing activity, highlighting the abuse of the cloud computing model for malicious purposes. The campaign involved the use of Google Cloud container URLs to host credential phishing pages with the aim of harvesting login information associated with Mercado Pago, an online payments platform popular in the LATAM region.

It's becoming evident that the legacy practice of signature-based threat detection needs to be improved for cloud security challenges. In this Help Net Security video, Jimmy Mesta, CTO at RAD Security, discusses a new proposed standard for creating behavioral fingerprints of open-source image behavior at runtime.

In the ever-evolving landscape of cybersecurity, cloud security has emerged as a critical concern for organizations worldwide for a few years now. Cloud security is sometimes misunderstood or underestimated.

AT&T has admitted that cyberattackers grabbed a load of its data for the second time this year, and if you think the first haul was big, you haven't seen anything: This latest one includes data on "Nearly all" AT&T wireless customers - and those served by mobile virtual network operators running on AT&T's network. Some customers could be at risk because "a subset" of records contained in that online storage included one or more cell tower identification numbers, allowing snoops to potentially roughly geolocate a customer whose data was stolen in the attack.

Snowflake? Snowflake AT&T has admitted that cyberattackers grabbed a load of its data for the second time this year, and if you think the first haul was big you haven't seen anything: This one...

A BlastRADIUS attack involves the attacker intercepting network traffic between a client, such as a router, and the RADIUS server. While MD5 is well-known to have weaknesses that allow attackers to generate collisions or reverse the hash, the researchers say that the BlastRADIUS attack "Is more complex than simply applying an old MD5 collision attack" and more advanced in terms of speed and scale.

A new advanced persistent threat (APT) group named CloudSorcerer abuses public cloud services to steal data from Russian government organizations in cyberespionage attacks. [...]

As the use of the cloud continues to be strategically vital to many organizations, cloud resources have become the biggest targets for cyberattacks, with SaaS applications (31%), cloud storage...