Security News

Immerse is Cloudflare’s premier annual conference in Southeast Asia Partner Content Cloudflare is excited to present Immerse, our flagship event designed to connect attendees directly with the...

If you needed yet another reminder of what happens when security basics go awry It's a good news day for organizations that don't leave their AWS environment files publicly exposed because infosec...
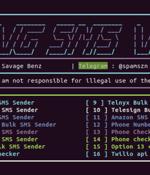
Malicious actors are using a cloud attack tool named Xeon Sender to conduct SMS phishing and spam campaigns on a large scale by abusing legitimate services. "Attackers can use Xeon to send...
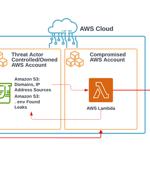
A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files that contain credentials associated with cloud and social media applications. Env files, out of which 7,000 belonged to organizations' cloud services and 1,500 variables are linked to social media accounts.

Cybercriminals are breaking into organizations' cloud storage containers, exfiltrating their sensitive data and, in several cases, have been paid off by the victim organizations to not leak or sell the stolen data. Exposed environment files hold keys to hosting cloud environments.

Maybe not surprising then that cloud security often tops the CISO agenda but it's a complex topic to keep on top of. Entirely free of charge, this annual meeting of top security minds is an opportunity for security professionals everywhere to learn from, and network with, experts and peers to build on their existing cloud security knowledge.

Scout Suite is an open-source, multi-cloud security auditing tool designed to assess the security posture of cloud environments. By leveraging the APIs provided by cloud vendors, Scout Suite collects and organizes configuration data, making it easier to identify potential risks.

Traditional cloud security issues often associated with cloud service providers are continuing to decrease in importance, according to the Top Threats to Cloud Computing 2024 report by the Cloud Security Alliance. "It's tempting to think that the reason the same issues have remained in the top spots since the report was last issued stems from a lack of progress in securing these features. The larger picture speaks to the importance placed on these vulnerabilities by organizations and the degrees to which they are working to build ever more secure and resilient cloud environments," said Michael Roza, co-chair, Top Threats Working Group.
TL;DR: Get speedy, secure and user-friendly cloud storage with a lifetime subscription to the FolderFort 1TB Storage Pro Plan - it's currently on sale at 68% off for just $80. Cloud data storage is one of the most useful and convenient developments in technology for businesses. Though it's certainly been around long enough, plans offering large amounts of storage still tend to be either slow or pricey.

Black Hat State-sponsored cyber spies and criminals are increasingly using legitimate cloud services to attack their victims, according to Symantec's threat hunters who have spotted three such operations over recent months, plus new data theft and other malware tools in development by these goons. This piece of malware used Microsoft's Graph API to communicate with the attacker's command and control server, hosted on Microsoft OneDrive.