Security News

New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant...

Cybersecurity researchers have shared details of a now-patched security vulnerability in Amazon Web Services (AWS) Managed Workflows for Apache Airflow (MWAA) that could be potentially exploited...
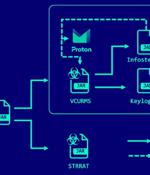
A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious Java-based downloader. “The attackers stored malware on public...

A malicious Python script known as SNS Sender is being advertised as a way for threat actors to send bulk smishing messages by abusing Amazon Web Services (AWS) Simple Notification Service (SNS)....

Prowler is an open-source security tool designed to assess, audit, and enhance the security of AWS, GCP, and Azure. "Easy to use from the command line with simple, understandable output, Prowler offers standard reporting formats like CSV and JSON, enabling users to thoroughly examine findings across any cloud provider, all in a uniform format. Its seamless integrations with Security Hub and S3 facilitate easy incorporation with other SIEMs, databases, and more. The ability to write custom checks and develop custom security frameworks is crucial for our expanding community," Toni de la Fuente, the creator of Prowler, told Help Net Security.

CloudFoxable is a capture-the-flag style learning platform you can deploy to your playground AWS account. It primarily targets current penetration testers seeking to learn exploitation of cloud-native attack paths, and cloud security experts aiming to practice offensive security techniques safely.

The Federal Bureau of Investigation and Cybersecurity & Infrastructure Security Agency warned in a joint advisory about a threat actor deploying a botnet that makes use of the Androxgh0st malware. The Androxgh0st malware was exposed in December 2022 by Lacework, a cloud security company.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warned that threat actors deploying the AndroxGh0st malware are creating a botnet for...

CISA and the FBI warned today that threat actors using Androxgh0st malware are building a botnet focused on cloud credential theft and using the stolen information to deliver additional malicious payloads. "Androxgh0st is a Python-scripted malware primarily used to target.env files that contain confidential information, such as credentials for various high profile applications," the two agencies cautioned.

Attackers usually gain access to an organization's cloud assets by leveraging compromised user access tokens obtained via phishing, by using malware, or by finding them in public code repositories. These are long-term access tokens associated with an AWS IAM or federated users.