Security News

Cybersecurity researchers have discovered severe cryptographic issues in various end-to-end encrypted (E2EE) cloud storage platforms that could be exploited to leak sensitive data. "The...

Cybersecurity researchers have gleaned additional insights into a nascent ransomware-as-a-service (RaaS) called Cicada3301 after successfully gaining access to the group's affiliate panel on the...

No attacks possible, but enough issues to cause concern Messaging giant WeChat uses a network protocol that the app's developers modified – and by doing so introduced security weaknesses,...
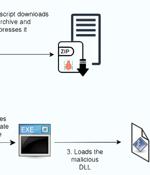
Cybersecurity researchers have disclosed a new malware campaign that delivers Hijack Loader artifacts that are signed with legitimate code-signing certificates. French cybersecurity company...

With an off-the-shelf D-Wave machine Chinese researchers claim they have found a way to use D-Wave's quantum annealing systems to develop a promising attack on classical encryption.…

Details have emerged about multiple security vulnerabilities in two implementations of the Manufacturing Message Specification (MMS) protocol that, if successfully exploited, could have severe...

Cybersecurity researchers are warning about active exploitation attempts targeting a newly disclosed security flaw in Synacor's Zimbra Collaboration. Enterprise security firm Proofpoint said it...

Cybersecurity researchers have flagged the discovery of a new post-exploitation red team tool called Splinter in the wild. Palo Alto Networks Unit 42 shared its findings after it discovered the...
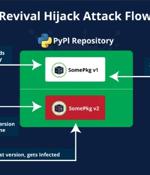
A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations. It has been codenamed...

This story seems straightforward. A city is the victim of a ransomware attack. They repeatedly lie to the media about the severity of the breach. A security researcher repeatedly proves their...