Security News
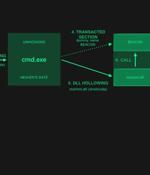
The threat actors behind a loader malware called HijackLoader have added new techniques for defense evasion, as the malware continues to be increasingly used by other threat actors to deliver...

The exposed secrets include hundreds of Stripe, GitHub/GitLab tokens, RSA private keys, OpenAI keys, AWS tokens, Twitch secret keys, cryptocurrency exchange keys, X tokens, and Slack and Discord webhooks. This approach shows how and where API secret keys and tokens are exposed in real-world settings, not only in code repositories.

Criminals could remotely tamper with the data that apps used by airplane pilots rely on to inform safe takeoff and landing procedures, according to fresh research. In a scenario that elicits strong memories of that nail-biting flight scene from Die Hard 2, researchers investigating electronic flight bags found the app used by Airbus pilots was vulnerable to remote data manipulation, given the right conditions.
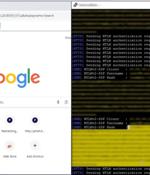
A now-patched security flaw in Microsoft Outlook could be exploited by threat actors to access NT LAN Manager (NTLM) v2 hashed passwords when opening a specially crafted file. The issue, tracked...

Security researchers analyzing the activity of the recently emerged 3AM ransomware operation uncovered close connections with infamous groups, such as the Conti syndicate and the Royal ransomware gang. The 3AM ransomware gang's activity was first documented publicly in mid-September when the Threat Hunter Team at Symantec, now part of Broadcom, revealed that they noticed threat actors switching to ThreeAM ransomware after failing to deploy the LockBit malware.

Microsoft says that a subgroup of the notorious APT35 Iranian-backed state hackers are targeting high-profile employees of research organizations and universities across Europe and the United States in spearphishing attacks pushing new MediaPL backdoor malware. MediaPL is a highly sophisticated malware strain designed to compromise the security of researchers and their data. The attackers have specifically targeted individuals involved in cutting-edge research, seeking unauthorized access to sensitive information. Microsoft's dedicated security teams have dissected the malware to better understand its functionality and devise effective countermeasures.

Ransomware victims already reeling from potential biz disruption and the cost of resolving the matter are now being subjected to follow-on extortion attempts by criminals posing as helpful security researchers. Researchers at Arctic Wolf Labs publicized two cases in which casulaties of the Royal and Akira ransomware gangs were targeted by a third party, believed to be the same individual or group in both scenarios, and extorted by a fake cyber samaritan.

A team of computer scientists led by the University of Massachusetts Amherst recently announced a new method for automatically generating whole proofs that can be used to prevent software bugs and verify that the underlying code is correct. "Reducing bugs in software, or even producing bug-free software, has been a holy grail of systems building for decades unfortunately, the state-of-the-practice in our society is that we expect all software to have bugs. Building bug-free software is just an incredibly difficult challenge."
When organizations get hit by ransomware and pay the crooks to decrypt the encrypted data and delete the stolen data, they can never be entirely sure the criminals will do as they promised. Even if an organization gets its data decrypted, they cannot be sure the stolen data has indeed been wiped and won't subsequently be used or sold.

Tactical and targeting overlaps have been discovered between the enigmatic advanced persistent threat (APT) called Sandman and a China-based threat cluster that's known to use a backdoor known as...