Security News

Telegram fixed a zero-day vulnerability in its Windows desktop application that could be used to bypass security warnings and automatically launch Python scripts. The next day, a proof of concept exploit was shared on the XSS hacking forum explaining that a typo in the source code for Telegram for Windows could be exploited to send Python.

This caused the file to automatically be executed by Python without a warning from Telegram like it does for other executables, and was supposed to do for this file if it wasn't for a typo. In a statement to BleepingComputer, Telegram rightfully disputes that the bug was a zero-click flaw but confirmed they fixed the "Issue" in Telegram for Windows to prevent Python scripts from automatically launching when clicked.
In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to...
Cybersecurity researchers are calling attention to the "democratization" of the phishing ecosystem owing to the emergence of Telegram as an epicenter for cybercrime, enabling threat actors to...

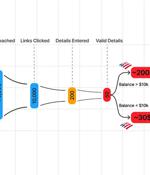
More details have emerged about a malicious Telegram bot called Telekopye that's used by threat actors to pull off large-scale phishing scams. "Telekopye can craft phishing websites, emails, SMS...

Telegram, the widely used messaging app, has unveiled an integrated crypto wallet feature, allowing users to effortlessly access their cryptocurrency holdings. The revelation came amidst the TOKEN2049 conference, where the TON Foundation and Telegram publicly announced their partnership.

An app with the name Signal Plus Messenger was available on Play for nine months and had been downloaded from Play roughly 100 times before Google took it down last April after being tipped off by security firm ESET. It was also available in the Samsung app store and on signalplus[. An app calling itself FlyGram was created by the same threat actor and was available through the same three channels.

At the time the researchers published their report, several malicious apps were still available for download through Google Play. The Telegram apps presented in Kaspersky's report are promoted as "Faster" alternatives to the regular app.
Spyware masquerading as modified versions of Telegram have been spotted in the Google Play Store that's designed to harvest sensitive information from compromised Android devices. The apps have been collectively downloaded millions of times before they were taken down by Google.

ESET researchers have identified two active campaigns targeting Android users, where the threat actors behind the tools for Telegram and Signal are attributed to the China-aligned APT group GREF. Most likely active since July 2020 and since July 2022, respectively for each malicious app, the campaigns have distributed the Android BadBazaar espionage code through the Google Play store, Samsung Galaxy Store, and dedicated websites posing as legitimate encrypted chat applications - the malicious apps are FlyGram and Signal Plus Messenger. Threat actors exploit fake Signal and Telegram apps.