Security News

Popular WordPress security plugin WP Ghost is vulnerable to a critical severity flaw that could allow unauthenticated attackers to remotely execute code and hijack servers. [...]

A critical security vulnerability has been disclosed in AMI's MegaRAC Baseboard Management Controller (BMC) software that could allow an attacker to bypass authentication and carry out...

Microsoft announced that it will drop support for the Remote Desktop app (available via the Microsoft Store) on May 27 and replace it with its new Windows App. [...]

The global transition to remote work has reshaped traditional workplace dynamics, introducing challenges and opportunities for cybersecurity teams. For CISOs and security professionals, embracing...

Elastic has rolled out security updates to address a critical security flaw impacting the Kibana data visualization dashboard software for Elasticsearch that could result in arbitrary code...
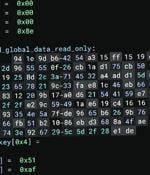
Universities and government organizations in North America and Asia have been targeted by a previously undocumented Linux malware called Auto-Color between November and December 2024, according to...

Cybersecurity researchers have disclosed a new type of name confusion attack called whoAMI that allows anyone who publishes an Amazon Machine Image (AMI) with a specific name to gain code...

The North Korean hacking group known as Kimsuky was observed in recent attacks using a custom-built RDP Wrapper and proxy tools to directly access infected machines. [...]

Cybersecurity researchers have called attention to a software supply chain attack targeting the Go ecosystem that involves a malicious package capable of granting the adversary remote access to...

Remote work is now an essential part of many businesses, requiring organizations to rethink how they provide secure and efficient access to corporate resources. Learn from TruGrid about the...