Security News

As corporate conglomerates, small businesses and brick-and-mortar shops fade away in favor of a distributed offsite workforce, companies and employees can profit from the greater convenience and efficiency provided by remote access. Combined with a bring your own device policy, remote access can lower equipment costs, reduce office overhead and facilitate employee productivity.

The notorious North Korea-linked threat actor known as the Lazarus Group has been attributed to a new global campaign that involves the opportunistic exploitation of security flaws in Log4j to...

Cybercriminals still prefer targeting open remote access products, or like to leverage legitimate remote access tools to hide their malicious actions, according to WatchGuard. "Threat actors continue using different tools and methods in their attack campaigns, making it critical for organizations to keep abreast of the latest tactics to fortify their security strategy," said Corey Nachreiner, chief security officer at WatchGuard.

Security researchers are warning that hackers are targeting multiple healthcare organizations in the U.S. by abusing the ScreenConnect remote access tool. [...]

The Everest ransomware group is stepping up its efforts to purchase access to corporate networks directly from employees amid what researchers believe to be a major transition for the cybercriminals. Everest ransomware group's message on its deep web blog advertising its intent to recruit corporate insiders.

This Remote Access Checklist from TechRepublic Premium should be used to ensure all employees have the requisite items, accounts, access and instructions needed for remote work. Resource Details Download for $9 or Access all downloads for $299/yr*.
A new remote access trojan called QwixxRAT is being advertised for sale by its threat actor through Telegram and Discord platforms. "Once installed on the victim's Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information," Uptycs said in a new report published today.

"The report shows 92% of survey respondents recognize the importance of adopting a zero trust architecture; however, it is concerning to see many organizations are still using a VPN for remote employee and third-party access, inadvertently providing a juicy attack surface for threat actors," said Deepen Desai, Global CISO and Head of Security Research, Zscaler. "Legacy firewall and VPN vendors are spinning virtual VPNs in the cloud and claiming that it is zero trust, and they go the extra length to hide the word"VPN". Customers need to ask the right questions to make sure that they are not getting a false sense of security with these virtualized legacy offerings in the cloud. In order to safeguard against evolving ransomware attacks, it is critical for organizations to eliminate the use of VPNs, prioritize user-to-app segmentation, and implement an in-line contextual data loss prevention engine with full TLS inspection," added Desai.

Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute Cloud (EC2) instances (virtual servers), as well as...
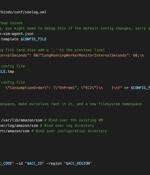
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services that allows the AWS Systems Manager Agent to be run as a remote access trojan on Windows and Linux environments. "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with SSM agent installed, to carry out malicious activities on an ongoing basis," Mitiga researchers Ariel Szarf and Or Aspir said in a report shared with The Hacker News.