Security News

Broadcom released security updates today to fix a high-severity authentication bypass vulnerability in VMware Tools for Windows. [...]

Europol has released its 2025 report on serious and organized crime in the EU. The EU Serious and Organised Crime Threat Assessment (EU-SOCTA) is based on intelligence from EU countries and global...
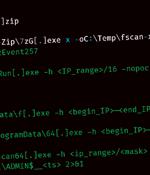
Threat hunters have uncovered a new threat actor named UAT-5918 that has been attacking critical infrastructure entities in Taiwan since at least 2023. "UAT-5918, a threat actor believed to be...

Malware peddlers are increasingly targeting users who are searching for free file converter services (websites) and tools, the FBI’s Denver Field Office has warned earlier this month. “To conduct...
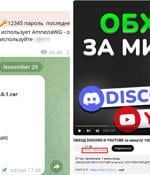
A new mass malware campaign is infecting users with a cryptocurrency miner named SilentCryptoMiner by masquerading it as a tool designed to circumvent internet blocks and restrictions around...

In recent years, collaboration tools have become an absolute necessity for remote and hybrid work. This primarily increased during the COVID-19 pandemic due to the impossibility of communicating...

The growth of AI-based technology has introduced new challenges, making remote identity verification systems more vulnerable to attacks, according to iProov. Innovative and easily accessible tools...

This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. Kunai: Open-source threat hunting tool...

Social engineering is advancing fast, at the speed of generative AI. This is offering bad actors multiple new tools and techniques for researching, scoping, and exploiting organizations. In a...

A China-based threat actor, tracked as Emperor Dragonfly and commonly associated with cybercriminal endeavors, has been observed using in a ransomware attack a toolset previously attributed to...