Security News

During the second day of Pwn2Own Berlin 2025, competitors earned $435,000 after exploiting zero-day bugs in multiple products, including Microsoft SharePoint, VMware ESXi, Oracle VirtualBox, Red...

Threat actors are leveraging an artificial intelligence (AI) powered presentation platform named Gamma in phishing attacks to direct unsuspecting users to spoofed Microsoft login pages. "Attackers...
The financially motivated threat actor known as FIN7 has been linked to a Python-based backdoor called Anubis (not to be confused with an Android banking trojan of the same name) that can grant...

The legacy domain for Microsoft Stream was hijacked to show a fake Amazon site promoting a Thailand casino, causing all SharePoint sites with old embedded videos to display it as spam. [...]

A newly uncovered ClickFix phishing campaign is tricking victims into executing malicious PowerShell commands that deploy the Havok post-exploitation framework for remote access to compromised...
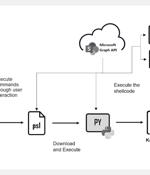
Cybersecurity researchers are calling attention to a new phishing campaign that employs the ClickFix technique to deliver an open-source command-and-control (C2) framework called Havoc. "The...

The cyber security firm reported in its latest annual report that their researchers found more than 30.4 million phishing emails last year.

Cybersecurity researchers have disclosed details of a now-patched vulnerability impacting the Microsoft SharePoint connector on Power Platform that, if successfully exploited, could allow threat...

Microsoft is working on fixing an ongoing and widespread Microsoft 365 outage that is impacting multiple services and features, including Exchange Online, Microsoft Teams, and SharePoint Online. [...]

A recently disclosed Microsoft SharePoint remote code execution (RCE) vulnerability tracked as CVE-2024-38094 is being exploited to gain initial access to corporate networks. [...]