Security News

Microsoft marks March 2022 Patch Tuesday with patches for 71 CVE-numbered vulnerabilities, including three previously unknown "Critical" ones and three "Important" ones that were already public. "If an attacker can lure an affected RDP client to connect to their RDP server, the attacker could trigger code execution on the targeted client," says Dustin Childs, with Trend Micro's Zero Day Initiative.

To protect client data during the ongoing conflicts, Cloudflare has removed all customer encryption keys from data centers located in Ukraine, Russia, and Belarus, and deployed its "Keyless SSL" technology. The second measure is the addition of a forceful configuration on all servers located in Ukraine, Belarus, and Russia, to automatically brick in the case of a power loss or internet connection disruption.

Microsoft says Windows Server security updates released on and since the January 2022 Patch Tuesday might prevent applications and network appliances from creating Netlogon secure channels if installed on domain controllers. Netlogon is a remote procedure call interface and Windows Server process that authenticates services and users on Windows domain-based networks.

A notification from the U.S. Cybersecurity Infrastructure and Security Agency warns that threat actors are exploiting vulnerabilities in Zabbix open-source tool for monitoring networks, servers, virtual machines, and cloud services. The agency is asking federal agencies to patch any Zabbix servers against security issues tracked as CVE-2022-23131 and CVE-2022-23134, to avoid "Significant risk" from malicious cyber actors.

The Cuba ransomware operation is exploiting Microsoft Exchange vulnerabilities to gain initial access to corporate networks and encrypt devices. Cybersecurity firm Mandiant tracks the ransomware gang as UNC2596 and the ransomware itself as COLDDRAW. However, the ransomware is more commonly known as Cuba, which is how BleepingComputer will reference them throughout this article.

Threat analysts have observed a new wave of attacks installing Cobalt Strike beacons on vulnerable Microsoft SQL Servers, leading to deeper infiltration and subsequent malware infections. The attacks start with threat actors scanning for servers with an open TCP port 1433, which are likely public-facing MS-SQL servers.
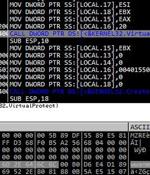
Vulnerable internet-facing Microsoft SQL Servers are being targeted by threat actors as part of a new campaign to deploy the Cobalt Strike adversary simulation tool on compromised hosts. "Attacks that target MS SQL servers include attacks to the environment where its vulnerability has not been patched, brute forcing, and dictionary attack against poorly managed servers," South Korean cybersecurity company AhnLab Security Emergency Response Center said in a report published Monday.

An Iranian-aligned hacking group tracked as TunnelVision was spotted exploiting Log4j on VMware Horizon servers to breach corporate networks in the Middle East and the United States. Security analysts at SentinelLabs who have been tracking the activity chose that name due to the group's heavy reliance on tunneling tools, which help them hide their activities from detecting solutions.

Microsoft announced the general availability of hotpatching for Windows Server Azure Edition core virtual machines allowing admins to install Windows security updates on supported VMs without requiring server restarts. The feature works with newly deployed Azure virtual machines running Windows Server 2022 Datacenter: Azure Edition Core Gen2 images and is available in all global Azure regions.

SquirrelWaffle - the newish malware loader that first showed up in September - once again got its scrabbly little claws into an unpatched Microsoft Exchange server to spread malspam with its tried-and-true trick of hijacking email threads. In a Tuesday post, Sophos analysts Matthew Everts and Stephen McNally said that typically, in SquirrelWaffle attacks - which typically entail the threat actors walking through holes left by unpatched, notorious, oft-picked-apart ProxyLogon and ProxyShell Exchange server vulnerabilities - the attack ends when those holes finally get patched, removing the attacker's ability to send emails through the server.