Security News

Russian threat actors have been launching phishing campaigns that exploit the legitimate "Linked Devices" feature in the Signal messaging app to gain unauthorized access to accounts of interest. [...]

The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing a novel technique to evade detection and maintain control over infected systems. This involves the use...

Cybersecurity researchers have flagged a credit card stealing malware campaign that has been observed targeting e-commerce sites running Magento by disguising the malicious content within image...

Hackers are launching attacks against Palo Alto Networks PAN-OS firewalls by exploiting a recently fixed vulnerability (CVE-2025-0108) that allows bypassing authentication. [...]

Cybersecurity researchers have disclosed a new type of name confusion attack called whoAMI that allows anyone who publishes an Amazon Machine Image (AMI) with a specific name to gain code...

Attackers are now targeting an authentication bypass vulnerability affecting SonicWall firewalls shortly after the release of proof-of-concept (PoC) exploit code. [...]

Palo Alto Networks has addressed a high-severity security flaw in its PAN-OS software that could result in an authentication bypass. The vulnerability, tracked as CVE-2025-0108, carries a CVSS...

Threat hunters have shed light on a new campaign targeting the foreign ministry of an unnamed South American nation with bespoke malware capable of granting remote access to infected hosts. The...
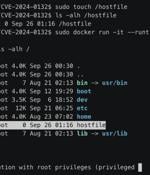
Cybersecurity researchers have discovered a bypass for a now-patched security vulnerability in the NVIDIA Container Toolkit that could be exploited to break out of a container's isolation...

The North Korea-linked threat actor known as Kimsuky has been observed using a new tactic that involves deceiving targets into running PowerShell as an administrator and then instructing them to...