Security News

Threat actors are using public exploits to pummel a critical zero-day remote code execution flaw that affects all versions of a popular collaboration tool used in cloud and hybrid server environments and allows for complete host takeover. Researchers from Volexity uncovered the flaw in Atlassian Confluence Server and Data Center software over the Memorial Day weekend after they detected suspicious activity on two internet-facing web servers belonging to a customer running the software, they said in a blog post published last week.

A suspected state-aligned threat actor has been attributed to a new set of attacks exploiting the Microsoft Office "Follina" vulnerability to target government entities in Europe and the U.S. Enterprise security firm Proofpoint said it blocked attempts at exploiting the remote code execution flaw, which is being tracked CVE-2022-30190. The payload, which manifests in the form of a PowerShell script, is Base64-encoded and functions as a downloader to retrieve a second PowerShell script from a remote server named "Seller-notification[.]live."

Proof-of-concept exploits for the actively exploited critical CVE-2022-26134 vulnerability impacting Atlassian Confluence and Data Center servers have been widely released this weekend. The vulnerability tracked as CVE-2022-26134 is a critical unauthenticated, remote code execution vulnerability exploited through OGNL injection and impacts all Atlassian Confluence and Data Center 2016 servers after version 1.3.0.

Check Point found attackers could transmit a specially designed radio packet to a nearby device to crash the firmware, ending that equipment's cellular connectivity, at least, presumably until it's rebooted. UNISOC is a 21-year-old chip designer based in China that spent the first 17 years of life known as Spreadtrum Communications, and that by 2011 was supplying chips for more than half of the mobile phones in the country.

The notorious Conti ransomware gang has working proof-of-concept code to exploit low-level Intel firmware vulnerabilities, according to Eclypsium researchers. Recently leaked Conti documents show the criminals developed the software more than nine months ago, and this is important because exploiting these kinds of weaknesses expands the extend and depth of an intrusion, the firmware security shop's analysis noted.

The botnet malware EnemyBot has added exploits to its arsenal, allowing it to infect and spread from enterprise-grade gear. "The threat group behind EnemyBot, Keksec, is well-resourced and has the ability to update and add new capabilities to its arsenal of malware on a daily basis," Ofer Caspi, a security researcher with Alien Labs, wrote in a blog post this month.
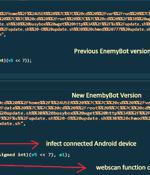
A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web servers, Android devices, and content management systems. "The malware is rapidly adopting one-day vulnerabilities as part of its exploitation capabilities," AT&T Alien Labs said in a technical write-up published last week.
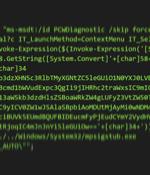
Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems. According to security researcher Kevin Beaumont, who dubbed the flaw "Follina," the maldoc leverages Word's remote template feature to fetch an HTML file from a server, which then makes use of the "Ms-msdt://" URI scheme to run the malicious payload. MSDT is short for Microsoft Support Diagnostics Tool, a utility that's used to troubleshoot and collect diagnostic data for analysis by support professionals to resolve a problem.

EnemyBot, a botnet based on code from multiple malware pieces, is expanding its reach by quickly adding exploits for recently disclosed critical vulnerabilities in web servers, content management systems, IoT, and Android devices. The botnet was first discovered in March by researchers at Securonix and by April, when analysis of newer samples emerged from Fortinet, EnemyBot had already integrated flaws for more than a dozen processor architectures.

EnemyBot, a botnet based on code from multiple malware pieces, is expanding its reach by quickly adding exploits for recently disclosed critical vulnerabilities in web servers, content management systems, IoT, and Android devices. Its main purpose is launching distributed denial-of-service attacks and the malware also has modules to scan for new target devices and infect them.