Security News

Fortinet has issued an alert warning that the Gafgyt botnet malware is actively trying to exploit a vulnerability in the end-of-life Zyxel P660HN-T1A router in thousands of daily attacks. [...]
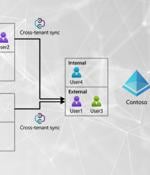
This attack vector enables an attacker operating in a compromised tenant to abuse a misconfigured Cross-Tenant Synchronization configuration and gain access to other connected tenants or deploy a rogue CTS configuration to maintain persistence within the tenant. Terminologies# Source tenant Tenant from where users & groups are getting synced Target tenant Tenant with resources where users & groups are getting synced Resources Microsoft applications and non-Microsoft applications CTS Abbreviation to reference 'Cross Tenant Synchronization' in this document CTA Abbreviation to reference 'Cross Tenant Access' in this document Compromised Account Adversaries initial point of access The Facilitator#.

The August 2023 Microsoft security updates are out, with 74 CVE-numbered bugs fixed. Intriguingly, if not confusingly, Microsoft's offical bug listing page is topped by two special items dubbed Exploitation Detected.
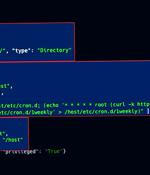
Exposed Kubernetes clusters are being exploited by malicious actors to deploy cryptocurrency miners and other backdoors. Cloud security firm Aqua, in a report shared with The Hacker News, said a majority of the clusters belonged to small to medium-sized organizations, with a smaller subset tied to bigger companies, spanning financial, aerospace, automotive, industrial, and security sectors.

A sophisticated Facebook phishing campaign has been observed exploiting a zero-day flaw in Salesforce's email services, allowing threat actors to craft targeted phishing messages using the company's domain and infrastructure. What makes the attack notable is that the phishing kit is hosted as a game under the Facebook apps platform using the domain apps.

Hackers are actively exploiting a 'BleedingPipe' remote code execution vulnerability in Minecraft mods to run malicious commands on servers and clients, allowing them to take control of the devices. BleedingPipe is a vulnerability found in many Minecraft mods caused by the incorrect use of deserialization in the 'ObjectInputStream' class in Java to exchange network packets between servers and clients.
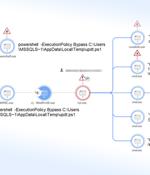
Mallox ransomware activities in 2023 have witnessed a 174% increase when compared to the previous year, new findings from Palo Alto Networks Unit 42 reveal. "Mallox ransomware, like many other ransomware threat actors, follows the double extortion trend: stealing data before encrypting an organization's files, and then threatening to publish the stolen data on a leak site as leverage to convince victims to pay the ransom fee," security researchers Lior Rochberger and Shimi Cohen said in a new report shared with The Hacker News.
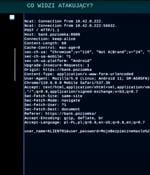
Threat actors are taking advantage of Android's WebAPK technology to trick unsuspecting users into installing malicious web apps on Android phones that are designed to capture sensitive personal information. "The link contained in the message led to a site that used WebAPK technology to install a malicious application on the victim's device."
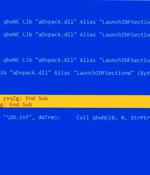
Microsoft Word documents exploiting known remote code execution flaws are being used as phishing lures to drop malware called LokiBot on compromised systems. The Word file that weaponizes CVE-2021-40444 contains an external GoFile link embedded within an XML file that leads to the download of an HTML file, which exploits Follina to download a next-stage payload, an injector module written in Visual Basic that decrypts and launches LokiBot.

Rockwell Automation says a new remote code execution exploit linked to an unnamed Advanced Persistent Threat group could be used to target unpatched ControlLogix communications modules commonly used in manufacturing, electric, oil and gas, and liquified natural gas industries.The company teamed up with the U.S. Cybersecurity and Infrastructure Security Agency to analyze the exploit linked to APT threat actors, but they have yet to share how they obtained it.