Security News

The threat actors behind the BlackByte ransomware group have been observed likely exploiting a recently patched security flaw impacting VMware ESXi hypervisors, while also leveraging various...

ESET researchers discovered a remote code execution vulnerability in WPS Office for Windows (CVE-2024-7262). APT-C-60, a South Korea-aligned cyberespionage group, was exploiting it to target East...

Cybersecurity researchers are calling attention to a new QR code phishing (aka quishing) campaign that leverages Microsoft Sway infrastructure to host fake pages, once again highlighting the abuse...
The China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of a recently disclosed high-severity security flaw...

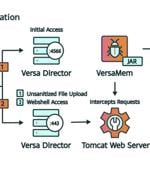
Details have emerged about a China-nexus threat group's exploitation of a recently disclosed, now-patched security flaw in Cisco switches as a zero-day to seize control of the appliance and evade...

Unknown attackers have deployed a newly discovered backdoor dubbed Msupedge on a university's Windows systems in Taiwan, likely by exploiting a recently patched PHP remote code execution...

A previously undocumented backdoor named Msupedge has been put to use against a cyber attack targeting an unnamed university in Taiwan. "The most notable feature of this backdoor is that it communicates with a command-and-control server via DNS traffic," the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News.

Cybersecurity researchers have shed light on a threat actor known as Blind Eagle that has persistently targeted entities and individuals in Colombia, Ecuador, Chile, Panama, and other Latin...

A file-sharing phishing attack is a unique type of phishing threat in which a cybercriminal poses as a known colleague or familiar file-hosting or e-signature solution and sends a target a malicious email containing a link to what appears to be a shared file or document. File-sharing phishing attacks would be a pressing issue regardless of volume, as one single successful attack can have costly consequences.

Cybersecurity researchers have uncovered a surge in malware infections stemming from malvertising campaigns distributing a loader called FakeBat. Attack chains propagating the malware make use of drive-by download techniques to push users searching for popular software toward bogus lookalike sites that host booby-trapped MSI installers.