Security News

New findings show that malicious actors could leverage a sneaky malware detection evasion technique and bypass endpoint security solutions by manipulating the Windows Container Isolation Framework. Microsoft's container architecture uses what's called a dynamically generated image to separate the file system from each container to the host and at the same time avoid duplication of system files.

VMware Aria Operations for Networks is vulnerable to a critical severity authentication bypass flaw that could allow remote attackers to bypass SSH authentication and access private endpoints. VMware Aria is a suite for managing and monitoring virtualized environments and hybrid clouds, enabling IT automation, log management, analytics generation, network visibility, security and capacity planning, and full-scope operations management.

Cybercriminals employ artificial intelligence to create complex email threats like phishing and business email compromise attacks, while modern email security systems use AI to counter these attacks, according to Perception Point and Osterman Research. Cybercriminals have shown rapid adoption of AI tools to their favor with 91.1% of organizations reporting that they have already encountered email attacks that have been enhanced by AI, and 84.3% expecting that AI will continue to be utilized to circumvent existing security systems.

The FBI is warning of a new tactic used by cybercriminals where they promote malicious "Beta" versions of cryptocurrency investment apps on popular mobile app stores that are then used to steal crypto. The threat actors submit the malicious apps to the mobile app stores as "Betas," meaning that they are in an early development phase and are meant to be used by tech enthusiasts or fans to test and submit feedback to developers before the software is officially released.

Threat actors are leveraging a technique called versioning to evade Google Play Store's malware detections and target Android users. Earlier this May, ESET discovered a screen recording app named "iRecorder - Screen Recorder" that remained innocuous for nearly a year after it was first uploaded to the Play Store before malicious changes were introduced sneakily to spy on its users.

Cybersecurity researchers have discovered a bypass for a recently fixed actively exploited vulnerability in some versions of Ivanti Endpoint Manager Mobile, prompting Ivanti to urge users to update to the latest version of the software. Tracked as CVE-2023-35082 and discovered by Rapid7, the issue "Allows unauthenticated attackers to access the API in older unsupported versions of MobileIron Core.".

IT software company Ivanti disclosed today a new critical security vulnerability in its MobileIron Core mobile device management software. "MobileIron Core 11.2 has been out of support since March 15, 2022. Therefore, Ivanti will not be issuing a patch or any other remediations to address this vulnerability in 11.2 or earlier versions. Upgrading to the latest version of Ivanti Endpoint Manager Mobile is the best way to protect your environment from threats," the company said.
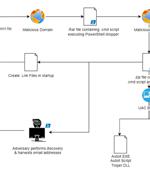
The financially motivated threat actors behind the Casbaneiro banking malware family have been observed making use of a User Account Control bypass technique to gain full administrative privileges on a machine, a sign that the threat actor is evolving their tactics to avoid detection and execute malicious code on compromised assets. Casbaneiro, also known as Metamorfo and Ponteiro, is best known for its banking trojan, which first emerged in mass email spam campaigns targeting the Latin American financial sector in 2018.

Adobe released an emergency ColdFusion security update that fixes critical vulnerabilities, including a fix for a new zero-day exploited in attacks. As part of today's out-of-band update, Adobe fixed three vulnerabilities: a critical RCE tracked as CVE-2023-38204, a critical Improper Access Control flaw tracked as CVE-2023-38205, and a moderate Improper Access Control flaw tracked as CVE-2023-38206.

Many still lack the necessary tools to investigate the security and organizational impact of these infections and effectively mitigate follow-on attacks - with 98% indicating better visibility into at-risk applications would significantly improve their security posture. Seemingly innocuous actions like these can inadvertently expose organizations to malware and follow-on attacks including ransomware stemming from the stolen access details.