Security News

The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and detection evasion techniques, enabling its operators to remotely interact with...

Security researchers found a new version of the Vultur banking trojan for Android that includes more advanced remote control capabilities and an improved evasion mechanism. A report from Fox-IT, part of the NCC Group, warns that a new, more evasive version of Vultur spreads to victims through a hybrid attack that relies on smishing and phone calls that trick the targets into installing a version of the malware that masquerades as the McAfee Security app.

Hackers hijacked the official contact email for the Belgian Grand Prix event and used it to lure fans to a fake website promising a €50 gift voucher. The Spa Gran Prix is a Formula 1 World Championship race held at the Circuit de Spa-Francorchamps in Stavelot, Belgium.

The threat actors behind the PixPirate Android banking trojan are leveraging a new trick to evade detection on compromised devices and harvest sensitive information from users in Brazil. The...

Users in Brazil are the target of a new banking trojan known as CHAVECLOAK that's propagated via phishing emails bearing PDF attachments. "This intricate attack involves the PDF downloading a ZIP...
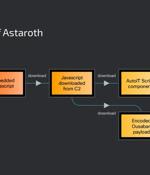
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka...

Security researchers are warning of hackers abusing the Google Cloud Run service to distribute massive volumes of banking trojans like Astaroth, Mekotio, and Ousaban. Google Cloud Run is lets users deploy frontend and backend services, websites or applications, handle workloads without the effort of managing an infrastructure or scaling.

Cybercriminals are targeting iOS users with malware that steals Face ID scans to break into and pilfer money from bank accounts - thought to be a world first. iOS target Android and iOS respectively, tricking users into performing biometric verification checks that are ultimately used to bypass the same checks employed by legitimate banking apps in Vietnam and Thailand - the geographic focus of these ongoing attacks.

A Chinese-speaking threat actor codenamed GoldFactory has been attributed to the development of highly sophisticated banking trojans, including a previously undocumented iOS malware called...

The threat actors behind the Mispadu banking Trojan have become the latest to exploit a now-patched Windows SmartScreen security bypass flaw to compromise users in Mexico. The attacks entail a new...