Security News

A threat group that targets corporate emails is delivering dropper malware through a novel technique that uses Microsoft Internet Information Services logs to send commands disguised as web access requests. The dropper, dubbed Geppei, is being used by a group Symantec threat researchers call Cranefly to install other undocumented malware.

Germany's Federal Criminal Police Office has arrested a 22-year-old student in Bavaria, who is suspected of being the administrator of 'Deutschland im Deep Web', one of the largest darknet markets in the country. The platform had already gone offline in March 2022, with 16,000 registered users, 28,000 posts, and 72 high-volume sellers of prohibited goods, including weapons and drugs.

The Cranefly hacking group, aka UNC3524, uses a previously unseen technique of controlling malware on infected devices via Microsoft Internet Information Services web server logs. Like any web server, when a remote user accesses a webpage, IIS will log the request to log files that contain the timestamp, source IP addresses, the requested URL, HTTP status codes, and more.

A 34-year-old U.K. national has been arraigned in the U.S. for operating a dark web marketplace called The Real Deal that specialized in the sales of hacking tools and stolen login credentials. Daniel Kaye, who went by a litany of pseudonyms Popopret, Bestbuy, UserL0ser, and Spdrman, has been charged with five counts of access device fraud and one count of money laundering conspiracy.

A notorious British hacker was arraigned on Wednesday by the U.S. Department of Justice for allegedly running the now defunct 'The Real Deal" dark web marketplace. [...]
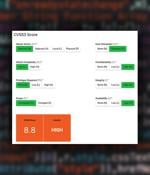
MyOpenVDP is a turnkey open-source solution allowing anyone to host their own vulnerability disclosure policy. Developed by YesWeHack, the web application is available on GitHub.
A hospital network in Wisconsin and Illinois fears visitor tracking code on its websites may have transmitted personal information on as many as 3 million patients to Meta, Google, and other third parties. Advocate Aurora Health reported the potential breach to the US government's Health and Human Services.
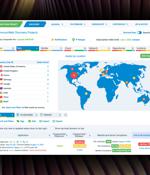
The underlying concept is simple and efficient: combining Attack Surface Management with dark web monitoring to boost their synergized value, making the "1+1=3" formula possible. Importantly, every single IT asset will be mapped onto the cyber threat landscape, visualizing the ongoing phishing campaigns targeting your customers or employees, dark web announcements selling access to your compromised systems or corporate data, rogue mobile applications usurping your corporate identity, stolen credentials from your applications or third-party systems processing your data, and IoCs found on your systems.

A free unofficial patch has been released through the 0patch platform to address an actively exploited zero-day flaw in the Windows Mark of the Web security mechanism. Windows automatically adds MotW flags to all documents and executables downloaded from untrusted sources, including files extracted from downloaded ZIP archives, using a special 'Zone.Id' alternate data stream.

A new phishing technique using Chrome's Application Mode feature allows threat actors to display local login forms that appear as desktop applications, making it easier to steal credentials. Because desktop applications are generally harder to spoof, users are less likely to treat them with the same caution they reserve for browser windows that are more widely abused for phishing.