Security News
Cybersecurity researchers have disclosed details of a now-patched privilege escalation vulnerability in Google Cloud Platform (GCP) Cloud Run that could have allowed a malicious actor to access...

BlueToolkit is an open-source tool that helps find security flaws in Bluetooth Classic devices. It runs known and custom exploits to test if a device is vulnerable. Right now, it includes 43...

Exploitation attempts targeting the CVE-2025-2825 vulnerability on internet-facing CrushFTP instances are happening, the Shadowserver Foundation has shared on Monday, and the attackers have been...

In what's an instance of hacking the hackers, threat hunters have managed to infiltrate the online infrastructure associated with a ransomware group called BlackLock, uncovering crucial...

Mozilla has released updates to address a critical security flaw impacting its Firefox browser for Windows, merely days after Google patched a similar flaw in Chrome that came under active...

CrushFTP has fixed a critical vulnerability (CVE-2025-2825) in its enterprise file transfer solution that could be exploited by remote, unauthenticated attackers to access vulnerable...
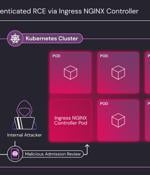
A set of five critical security shortcomings have been disclosed in the Ingress NGINX Controller for Kubernetes that could result in unauthenticated remote code execution, putting over 6,500...

A critical vulnerability (CVE-2025-29927) in the open source Next.js framework can be exploited by attackers to bypass authorization checks and gain unauthorized access to web pages they should no...

A critical security flaw has been disclosed in the Next.js React framework that could be potentially exploited to bypass authorization checks under certain conditions. The vulnerability, tracked...

A vulnerability (CVE-2024-48248) in NAKIVO Backup and Replication, a backup, ransomware protection and disaster recovery solution designed for organizations of all sizes and managed service...