Security News

VMware has released security updates to address three critical severity vulnerabilities in the Workspace ONE Assist solution that enable remote attackers to bypass authentication and elevate privileges to admin. Workspace ONE Assist provides remote control, screen sharing, file system management, and remote command execution to help desk and IT staff remotely access and troubleshoot devices in real time from the Workspace ONE console.

Proof-of-concept exploit code is now available for a pre-authentication remote code execution vulnerability allowing attackers to execute arbitrary code remotely with root privileges on unpatched Cloud Foundation and NSX Manager appliances. The flaw is in the XStream open-source library used by the two VMware products and was assigned an almost maximum CVSSv3 base score of 9.8/10 by VMware.

VMware on Tuesday shipped security updates to address a critical security flaw in its VMware Cloud Foundation product. "Due to an unauthenticated endpoint that leverages XStream for input serialization in VMware Cloud Foundation, a malicious actor can get remote code execution in the context of 'root' on the appliance," the company said in an advisory.

VMware has released security updates today to fix a critical vulnerability in VMware Cloud Foundation, a hybrid cloud platform for running enterprise apps in private or public environments. The flaw is in the XStream open-source library used by Cloud Foundation and has an almost maximum CVSSv3 base score of 9.8/10 assigned by VMware.

Security researchers observed malicious campaigns leveraging a critical vulnerability in VMware Workspace One Access to deliver various malware, including the RAR1Ransom tool that locks files in password-protected archives. Researchers at cybersecurity company Fortinet noticed in the newest campaigns that the threat actors deployed the Mira botnet for distributed denial-of-service attacks, the GuardMiner cryptocurrency miner, and the RAR1Ransom tool.

A now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both cryptocurrency miners and ransomware on affected machines. "The attacker intends to utilize a victim's resources as much as possible, not only to install RAR1Ransom for extortion, but also to spread GuardMiner to collect cryptocurrency," Fortinet FortiGuard Labs researcher Cara Lin said in a Thursday report.

Over 45,000 VMware ESXi servers inventoried by Lansweeper just reached end-of-life, with VMware no longer providing software and security updates unless companies purchase an extended support contract. As of October 15, 2022, VMware ESXi 6.5 and VMware ESXi 6.7 reached end-of-life and will only receive technical support but no security updates, putting the software at risk of vulnerabilities.

VMware informed customers today that vCenter Server 8.0 is still waiting for a patch to address a high-severity privilege escalation vulnerability disclosed in November 2021. VMware says this flaw can only be exploited by attackers using a vector network adjacent to the targeted server as part of high-complexity attacks requiring low privileges and no user interaction.
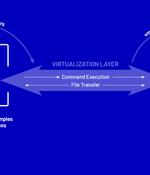
Threat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems and evade detection. Google's Mandiant threat intelligence division referred to it as a "Novel malware ecosystem" that impacts VMware ESXi, Linux vCenter servers, and Windows virtual machines, allowing attackers to maintain persistent access to the hypervisor as well as execute arbitrary commands.

Hackers have found a new method to establish persistence on VMware ESXi hypervisors to control vCenter servers and virtual machines for Windows and Linux while avoiding detection.A modified level of trust is not enough for the ESXi system to accept it by default but the attacker also used the '-force' flag to install the malicious VIBs.