Security News

A now-patched security flaw in the vm2 JavaScript sandbox module could be abused by a remote adversary to break out of security barriers and perform arbitrary operations on the underlying machine. "A threat actor can bypass the sandbox protections to gain remote code execution rights on the host running the sandbox," GitHub said in an advisory published on September 28, 2022.
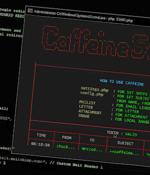
"This platform has an intuitive interface and comes at a relatively low cost while providing a multitude of features and tools to its criminal clients to orchestrate and automate core elements of their phishing campaigns," Mandiant said in a new report. Some of the core features offered by the platform comprise the ability to craft customized phishing kits, manage redirect pages, dynamically generate URLs that host the payloads, and track the success of the campaigns.

A new piece of research has detailed the increasingly sophisticated nature of the malware toolset employed by an advanced persistent threat group named Earth Aughisky. "Over the last decade, the group has continued to make adjustments in the tools and malware deployments on specific targets located in Taiwan and, more recently, Japan," Trend Micro disclosed in a technical profile last week.

Researchers have disclosed details about a now-patched high-severity security flaw in Packagist, a PHP software package repository, that could have been exploited to mount software supply chain attacks. Packagist is used by the PHP package manager Composer to determine and download software dependencies that are included by developers in their projects.
The recently discovered Linux-Based ransomware strain known as Cheerscrypt has been attributed to a Chinese cyber espionage group known for operating short-lived ransomware schemes. "This reinforces claims that the 'Emperor Dragonfly' ransomware operators are based in China."
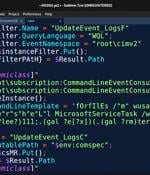
A new covert attack campaign singled out multiple military and weapons contractor companies with spear-phishing emails to trigger a multi-stage infection process designed to deploy an unknown payload on compromised machines. "The attack was carried out starting in late summer 2022 targeting at least two high-profile military contractor companies," Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in an analysis.

A new, multi-functional Go-based malware dubbed Chaos has been rapidly growing in volume in recent months to ensnare a wide range of Windows, Linux, small office/home office routers, and enterprise servers into its botnet. "Chaos functionality includes the ability to enumerate the host environment, run remote shell commands, load additional modules, automatically propagate through stealing and brute-forcing SSH private keys, as well as launch DDoS attacks," researchers from Lumen's Black Lotus Labs said in a write-up shared with The Hacker News.

The Council explored the state of Chinese infosec research in the context of the 2021 introduction of "Regulations on the Management of Security Vulnerabilities of Network Products" that require local researchers to report any vulns they find to local authorities. A ban on Chinese researchers participating in international infosec competitions is thought to have been imposed for similar reasons.

At least three alleged hacktivist groups working in support of Russian interests are likely doing so in collaboration with state-sponsored cyber threat actors, according to Mandiant. The Google-owned threat intelligence and incident response firm said with moderate confidence that "Moderators of the purported hacktivist Telegram channels 'XakNet Team,' 'Infoccentr,' and 'CyberArmyofRussia Reborn' are coordinating their operations with Russian Main Intelligence Directorate-sponsored cyber threat actors."
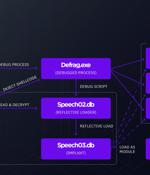
The cybersecurity firm codenamed the group Metador in reference to a string "I am meta" in one of their malware samples and because of Spanish-language responses from the command-and-control servers. The threat actor is said to have primarily focused on the development of cross-platform malware in its pursuit of espionage aims.