Security News
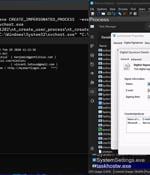
New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and...

BLACK HAT ASIA Researchers at US/Israeli infosec outfit SafeBreach last Friday discussed flaws in Microsoft and Kaspersky security products that can potentially allow the remote deletion of files. Speaking at the Black Hat Asia conference in Singapore, SafeBreach's VP of Security Research Tomer Bar and security researcher Shmuel Cohen explained that Microsoft Defender and Kaspersky's Endpoint Detection and Response can be made to detect false positive indicators of malicious files - and then to delete them.

Cybersecurity researchers have disclosed what they say is the "first native Spectre v2 exploit" against the Linux kernel on Intel systems that could be exploited to read sensitive data from the...

Hosting the Cybercrime Atlas in the World Economic Forum creates the space to experiment with how we enable disruption collaborations - giving the Cybercrime Atlas participants access to the expertise and ideas of the Forums' Partnership Against Cybercrime community. This was a turning point as it answered one of the first questions posed by the Cybercrime Atlas community: can we create new and actionable intelligence relying on open-source information and, by working collectively, can we build insights that match or exceed those created by the community members working in isolation? The answer to both of these questions is a resounding "Yes".

Multiple security vulnerabilities have been disclosed in LG webOS running on its smart televisions that could be exploited to bypass authorization and gain root access on the devices.The findings come from Romanian cybersecurity firm Bitdefender, which discovered and reported the flaws in November 2023. The issues were fixed by LG as part of updates released on March 22, 2024.

Multiple China-nexus threat actors have been linked to the zero-day exploitation of three security flaws impacting Ivanti appliances (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893). The...

Ivanti has fixed a critical RCE vulnerability in Ivanti Standalone Sentry that has been reported by researchers with the NATO Cyber Security Centre. The vulnerability affects all supported version of Ivanti Standalone Sentry as well as older, unsupported ones.

Details have been made public about a now-patched high-severity flaw in Kubernetes that could allow a malicious attacker to achieve remote code execution with elevated privileges under specific...

Google's Gemini large language model (LLM) is susceptible to security threats that could cause it to divulge system prompts, generate harmful content, and carry out indirect injection attacks. The...

Security researchers have created a knowledge base repository for attack and defense techniques based on improperly setting up Microsoft's Configuration Manager, which could allow an attacker to execute payloads or become a domain controller. At the SO-CON security conference today, SpecterOps researchers Chris Thompson and Duane Michael announced the release of Misconfiguration Manager, a repository with attacks based on faulty MCM configurations that also provides resources for defenders to harden their security stance.