Security News

CISA warns that attackers are now exploiting a Microsoft SharePoint code injection vulnerability that can be chained with a critical privilege escalation flaw for pre-auth remote code execution attacks. These two SharePoint Server security vulnerabilities can be chained by unauthenticated attackers to gain RCE on unpatched servers, as STAR Labs researcher Nguyễn Tiến Giang demonstrated during last year's March 2023 Pwn2Own contest in Vancouver.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a security flaw impacting the Microsoft Sharepoint Server to its Known Exploited Vulnerabilities (KEV) catalog based on...
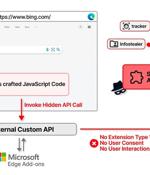
A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users' systems and carry out malicious actions. "This flaw could have...

The German national cybersecurity authority warned on Tuesday that it found at least 17,000 Microsoft Exchange servers in Germany exposed online and vulnerable to one or more critical security vulnerabilities. According to the German Federal Office for Information Security, around 45,000 Microsoft Exchange servers in Germany have Outlook Web Access enabled and are accessible from the Internet.

According to the report, titled Mission Critical: Unlocking the UK AI Opportunity Through Cybersecurity, cyberattacks currently cost the U.K. an estimated £87 billion each year. In a foreword to this new report, Microsoft UK CEO Claire Barclay said the U.K. could only meet its AI aspirations if businesses invested in cybersecurity processes and upgraded their security toolkits to match those of bad actors.

Around 12% of the 45,000 or so Microsoft Exchange servers in Germany that can be accessed from the Internet without restrictions "Are so outdated that security updates are no longer offered for them," the German Federal Office for Information Security has warned today. The BSI worries about attackers breaching those servers by exploiting CVE-2024-21410, a critical elevation of privilege bug that allows attackers to learn a targeted user's NTLM credentials and "Relay" them to authenticate themselves to a vulnerable Exchange Server as the user.

Cybercriminals have been increasingly using a new phishing-as-a-service platform named 'Tycoon 2FA' to target Microsoft 365 and Gmail accounts and bypass two-factor authentication protection. Tycoon 2FA attacks involve a multi-step process where the threat actor steals session cookies by using a reverse proxy server hosting the phishing web page, which intercepts the victim's input and relays them to the legitimate service.

In January 2024, Microsoft discovered they’d been the victim of a hack orchestrated by Russian-state hackers Midnight Blizzard (sometimes known as Nobelium). The concerning detail about this case...

ALSO: Viasat hack wiper malware is back, users are the number one cause of data loss, and critical vulns Infosec in brief If your Windows domain controllers have been crashing since a security...

Microsoft plans to limit access to over fifty cloud products for Russian organizations by the end of March as part of the sanctions requirements against the country issued by EU regulators last December. "After March 20, 2024, you will not be able to access those Microsoft products or services, or any data stored in them." - Microsoft.