Security News
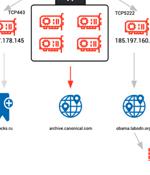
Cybersecurity researchers are calling attention to a free-to-use browser automation framework that's being increasingly used by threat actors as part of their attack campaigns. The U.S. cybersecurity company said it observed command-and-control IP addresses associated with malware such as Bumblebee, BlackGuard, and RedLine Stealer establishing connections to the downloads subdomain of Bablosoft, the maker of the Browser Automation Studio.
NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration. "Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as of May 2022," CrowdStrike said in a Wednesday report.

A new framework for assessing the privacy, technical security, usability and clinical assurance and safety of digital health technologies has been created by the American College of Physicians, the American Telemedicine Association and ORCHA, the Organization for the Review of Care and Health Applications. The Digital Health Assessment Framework is intended to be an open framework, accessible for anyone to use, to support the adoption of high-quality digital health technologies and help healthcare professionals and patients make better-informed decisions about which digital health tools - including mobile apps and web-based tools - best suit their needs.

NET Framework versions signed using the insecure Secure Hash Algorithm 1 will reach their end of life this month. NET. "On April 26, 2022, the.NET Framework 4.5.2, 4.6, and 4.6.1 will reach end of support, and after this date, Microsoft will no longer provide updates including security fixes and technical support for these versions," Microsoft said in a Windows message center update.

The maintainers of Spring Framework have released an emergency patch to address a newly disclosed remote code execution flaw that, if successfully exploited, could allow an unauthenticated attacker to take control of a targeted system. Tracked as CVE-2022-22965, the high-severity flaw impacts Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and other older, unsupported versions.

Another Java Remote Code Execution vulnerability has reared its head, this time in the popular Spring Framework and, goodness, it's a nasty one. This is a severe remote code execution zero day that can be accessed over HTTP or HTTPS. "Spring have acknowledged the vulnerability and released 5.3.18 and 5.2.20 to patch the issue," said Sonatype, "We recommend an immediate upgrade for all users."

A zero-day remote code execution vulnerability has come to light in the Spring framework shortly after a Chinese security researcher briefly leaked a proof-of-concept exploit on GitHub before deleting their account. According to cybersecurity firm Praetorian, the unpatched flaw impacts Spring Core on Java Development Kit versions 9 and later and is a bypass for another vulnerability tracked as CVE-2010-1622, enabling an unauthenticated attacker to execute arbitrary code on the target system.

A new zero-day vulnerability in the Spring Core Java framework called 'Spring4Shell' has been publicly disclosed, allowing unauthenticated remote code execution on applications. Spring is a very popular application framework that allows software developers to quickly and easily develop Java applications with enterprise-level features.

GTC Nvidia teased several updates to its Morpheus AI security framework at GTC this week, and also announced it would make the application framework generally available in April. In addition to releasing a pre-built version of Morpheus, Nvidia will also publish the framework's full source code on GitHub to allow developers to modify Morpheus and build security applications on top of the software.

The European Systemic Risk Board proposed a new systemic cyber incident coordination framework that would allow EU relevant authorities to coordinate better when responding to major cross-border cyber incidents impacting the Union's financial sector. ESRB is an independent EU body established in 2010 that oversees the European Union's financial system to prevent and mitigate systemic risk.