Security News

Hackers are exploiting a critical vulnerability that affects all D-Link DIR-859 WiFi routers to collect account information from the device, including passwords. Although D-Link DIR-859 WiFi router model reached end-of-life and no longer receives any updates, the vendor still released a security advisory explaining that the flaw exists in the "Fatlady.php" file of the device, affects all firmware versions, and allows attackers to leak session data, achieve privilege escalation, and gain full control via the admin panel.

Security researchers have shed more light on the cryptocurrency mining operation conducted by the 8220 Gang by exploiting known security flaws in the Oracle WebLogic Server. "The threat actor...

A group of security researchers from the Graz University of Technology have demonstrated a new side-channel attack known as SnailLoad that could be used to remotely infer a user's web activity....

A critical SQL injection vulnerability in Fortra FileCatalyst Workflow has been patched; a PoC exploit is already available online. Fortra FileCatalyst is an enterprise software solution for accellerated, UDP-based file transfer of large files.

The Fortra FileCatalyst Workflow is vulnerable to an SQL injection vulnerability that could allow remote unauthenticated attackers to create rogue admin users and manipulate data on the...
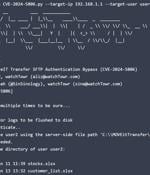
A newly disclosed critical security flaw impacting Progress Software MOVEit Transfer is already seeing exploitation attempts in the wild shortly after details of the bug were publicly disclosed....
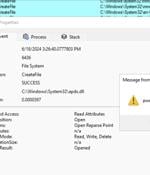
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Highlights Zero-day exploits are vulnerabilities in software or hardware that are unknown to the vendor or developer, so there is no patch or fix available at the time of their discovery. The most infamous cases of zero-day exploits include the MOVEit and Stuxnet vulnerabilities.

The Kraken crypto exchange disclosed today that alleged security researchers exploited a zero-day website bug to steal $3 million in cryptocurrency and then refused to return the funds. The hack was disclosed by Kraken Chief Security Officer Nick Percoco on X, explaining that the exchange's security team received a vague bug report on June 9th about an "Extremely critical" that allowed anyone to increase the balances in a Kraken wallet artificially.