Security News
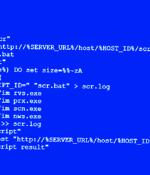
An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO high-performance object storage system to achieve unauthorized code execution on affected servers. Cybersecurity and incident response firm Security Joes said the intrusion leveraged a publicly available exploit chain to backdoor the MinIO instance.

Administrators of Citrix NetScaler ADC and Gateway appliances should check for evidence of installed webshells even if they implemented fixes for CVE-2023-3519 quickly: A recent internet scan by Fox-IT researchers has revealed over 1,800 backdoored NetScaler devices, 69% of which have been patched for the flaw. CVE-2023-3519 exploited to drop webshells on NetScaler devices.

Key factors for effective security automationIn this Help Net Security interview, Oliver Rochford, Chief Futurist at Tenzir, discusses how automation can be strategically integrated with human expertise, the challenges in ensuring data integrity, and the considerations when automating advanced tasks. MikroTik vulnerability could be used to hijack 900,000 routersA privilege escalation vulnerability could allow attackers to commandeer up to 900,000 MikroTik routers, says VulnCheck researcher Jacob Baines.

The number of data compromises reported in the U.S. in the H1 of 2023 is higher than the total compromises reported every year between 2005 and 2020, except for 2017, according to Identity Theft Resource Center. For the H1 ending June 30, 2023, there were 1,393 data compromises reported, including 951 in the Q2. Since 2005, only the full years of 2017, 2021 and 2022 have exceeded the number of compromises recorded in the first six months of 2023.

The Russia-linked threat actor known as Gamaredon has been observed conducting data exfiltration activities within an hour of the initial compromise. "As a vector of primary compromise, for the most part, emails and messages in messengers are used, in most cases, using previously compromised accounts," the Computer Emergency Response Team of Ukraine said in an analysis of the group published last week.

Attackers use various tactics to access sensitive information, such as email account compromise and using a legitimate email address to initiate the attack. In a more insidious attack, an attacker may compromise an existing employee's email account from the inside.

The compromise of PBI Research and The Berwyn Group's MOVEit installation has resulted in the theft of data belonging to several pension systems and insurance companies - and millions of their users. The fallout from the PBI Research MOVEit compromise.

A February 2023 generative AI survey of 1,000 executives revealed that 49% of respondents use ChatGPT now, and 30% plan to tap into the ubiquitous generative AI tool soon. 1 - Threat Actors Can Exploit Generative AI to Dupe SaaS Authentication Protocols #. As ambitious employees devise ways for AI tools to help them accomplish more with less too, do cybercriminals.

A report from the Microsoft Defender Experts reveals a new multi-staged adversary in the middle phishing attack combined with a business email compromise attack targeting banking and financial institutions. The phishing email impersonates one of the target's trusted vendors to appear more legitimate and blend with legitimate email traffic and bypass detections, especially when an organization has policies to automatically allow emails from trusted vendors.

TechRepublic Premium Bring your own device policy PURPOSE The purpose of this Bring your own device policy from TechRepublic Premium is to provide requirements for BYOD usage and establish the steps that both users and the IT department should follow to initialize, support and remove devices from company access. These requirements must be followed as documented in order to protect company systems .....