Security News

Key factors for effective security automationIn this Help Net Security interview, Oliver Rochford, Chief Futurist at Tenzir, discusses how automation can be strategically integrated with human expertise, the challenges in ensuring data integrity, and the considerations when automating advanced tasks. MikroTik vulnerability could be used to hijack 900,000 routersA privilege escalation vulnerability could allow attackers to commandeer up to 900,000 MikroTik routers, says VulnCheck researcher Jacob Baines.

A privilege escalation vulnerability (CVE-2023-30799) could allow attackers to commandeer up to 900,000 MikroTik routers, says VulnCheck researcher Jacob Baines. While exploting it does require...

A severe privilege escalation issue impacting MikroTik RouterOS could be weaponized by remote malicious actors to execute arbitrary code and seize full control of vulnerable devices. Cataloged as CVE-2023-30799, the shortcoming is expected to put approximately 500,000 and 900,000 RouterOS systems at risk of exploitation via their web and/or Winbox interfaces, respectively, VulnCheck disclosed in a Tuesday report.

A critical severity 'Super Admin' privilege elevation flaw puts over 900,000 MikroTik RouterOS routers at risk, potentially enabling attackers to take full control over a device and remain undetected. The Mikrotik CVE-2023-30799 vulnerability was first disclosed without an identifier in June 2022, and MikroTik fixed the issue in October 2022 for RouterOS stable and on July 19, 2023, for RouterOS Long-term.

"The C2 server serves as a botnet-as-a-service controlling nearly 230,000 vulnerable MikroTik routers," Avast's senior malware researcher, Martin Hron, said in a write-up, potentially linking it to what's now called the M?ris botnet. The botnet is known to exploit a known vulnerability in the Winbox component of MikroTik routers, enabling the attackers to gain unauthenticated, remote administrative access to any affected device.
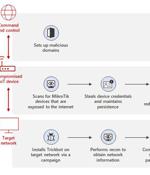
Microsoft on Wednesday detailed a previously undiscovered technique put to use by the TrickBot malware that involves using compromised Internet of Things devices as a go-between for establishing communications with the command-and-control servers. "By using MikroTik routers as proxy servers for its C2 servers and redirecting the traffic through non-standard ports, TrickBot adds another persistence layer that helps malicious IPs evade detection by standard security systems," Microsoft's Defender for IoT Research Team and Threat Intelligence Center said.

Microsoft released a scanner that detects MikroTik routers hacked by the TrickBot gang to act as proxies for command and control servers. For years, TrickBot has used IoT devices, such as routers, to act as a proxy between an infected device and command and control servers.

MikroTik routers are getting compromised to serve as communication proxies for Trickbot malware, to enable Trickbot-affected devices to communicate with their their C2 server in a way that standard network defense systems won't detect, Microsoft researchers have found. Its controllers are also constantly trying new tricks to allow the malware to persist on infected systems and keep communication with C2 servers uninterrupted.

At least 300,000 IP addresses associated with MikroTik devices have been found vulnerable to multiple remotely exploitable security vulnerabilities that have since been patched by the popular supplier of routers and wireless ISP devices. "This has made MikroTik devices a favorite among threat actors who have commandeered the devices for everything from DDoS attacks, command-and-control, traffic tunneling, and more."

Due to the sheer number of devices in use, their high power and numerous known vulnerabilities within them, threat actors have been using MikroTik devices for years as the command center from which to launch numerous attacks, researchers said. Eclypsium researchers began exploring the how and why of the weaponization of MikroTik devices in September, based on previous research into how TrickBot threat actors used compromised routers as command-and-control infrastructure.