Security News > 2022 > March > TrickBot Malware Abusing MikroTik Routers as Proxies for Command-and-Control
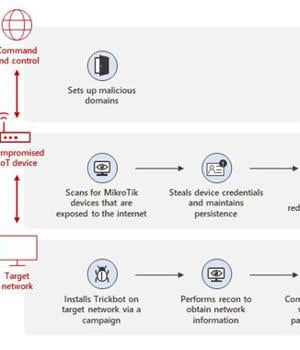
Microsoft on Wednesday detailed a previously undiscovered technique put to use by the TrickBot malware that involves using compromised Internet of Things devices as a go-between for establishing communications with the command-and-control servers.
"By using MikroTik routers as proxy servers for its C2 servers and redirecting the traffic through non-standard ports, TrickBot adds another persistence layer that helps malicious IPs evade detection by standard security systems," Microsoft's Defender for IoT Research Team and Threat Intelligence Center said.
The expansion to TrickBot's capabilities comes amid reports of its infrastructure going offline, even as the botnet has continually refined its features to make its attack framework durable, evade reverse engineering, and maintain the stability of its C2 servers.
Specifically, the new method identified by MSTIC involves leveraging hacked IoT devices such as routers from MikroTik to "Create a line of communication between the TrickBot-affected device and the C2 server."
"As security solutions for conventional computing devices continue to evolve and improve, attackers will explore alternative ways to compromise target networks," the researchers said.
"Attack attempts against routers and other IoT devices are not new, and being unmanaged, they can easily be the weakest links in the network."
News URL
https://thehackernews.com/2022/03/trickbot-malware-abusing-hacked-iot.html
Related news
- TheMoon malware infects 6,000 ASUS routers in 72 hours for proxy service (source)
- New Cuttlefish malware infects routers to monitor traffic for credentials (source)
- New Cuttlefish Malware Hijacks Router Connections, Sniffs for Cloud Credentials (source)
- New SOHO router malware aims for cloud accounts, internal company resources (source)