Security News

How to protect your organization's single sign-on credentials from compromise. Single sign-on, or SSO, is considered an effective method of authentication because it reduces the need for passwords and lets users authenticate across different applications and systems with just one single set of credentials.

American Airlines has notified customers of a recent data breach after attackers compromised an undisclosed number of employee email accounts and gained access to sensitive personal information. American Airlines discovered the breach on July 5th, immediately secured the impacted email accounts, and hired a cybersecurity forensic firm to investigate the security incident.
A hacktivist collective called GhostSec has claimed credit for compromising as many as 55 Berghof programmable logic controllers used by Israeli organizations as part of a "Free Palestine" campaign. "The group pivoted from their regular operations and started to target multiple Israeli companies, presumably gaining access to various IoT interfaces and ICS/SCADA systems, which led to possible disruptions," Cyberint noted on July 14.

To protect the victim's account, the organization had implemented Microsoft MFA through the Microsoft Authenticator app, which should have stopped any use of stolen credentials. Microsoft MFA doesn't always require a second form of authentication.

How a business email compromise scam spoofed the CFO of a major corporation. Business email compromise attacks work by using a standard phishing scheme and then lending it authority by impersonating a trusted and often high-ranking individual associated with the targeted organization.

The threat actor behind the SolarWinds supply chain attack has been linked to yet another "Highly targeted" post-exploitation malware that could be used to maintain persistent access to compromised environments. "Nobelium remains highly active, executing multiple campaigns in parallel targeting government organizations, non-governmental organizations, intergovernmental organizations, and think tanks across the US, Europe, and Central Asia," Microsoft said.

PyPI, the official third-party software repository for Python packages, is warning about a phishing campaign targeting its users. "We have additionally determined that some maintainers of legitimate projects have been compromised, and malware published as the latest release for those projects. These releases have been removed from PyPI and the maintainer accounts have been temporarily frozen," the PyPI team noted.

The malware loader known as Bumblebee is being increasingly co-opted by threat actors associated with BazarLoader, TrickBot, and IcedID in their campaigns to breach target networks for post-exploitation activities. "Bumblebee operators conduct intensive reconnaissance activities and redirect the output of executed commands to files for exfiltration," Cybereason researchers Meroujan Antonyan and Alon Laufer said in a technical write-up.

Zeppelin ransomware is back and employing new compromise and encryption tactics in its recent campaigns against various vertical industries-particularly healthcare-as well as critical infrastructure organizations, the feds are warning. Zeppelin also appears to have a new multi-encryption tactics, executing the malware more than once within a victim's network and creating different IDs and file extensions for multiple instances attack, according to the CISA. "This results in the victim needing several unique decryption keys," according to the advisory.
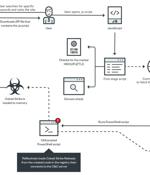
The operators of the Gootkit access-as-a-service malware have resurfaced with updated techniques to compromise unsuspecting victims. "In the past, Gootkit used freeware installers to mask malicious files; now it uses legal documents to trick users into downloading these files," Trend Micro researchers Buddy Tancio and Jed Valderama said in a write-up last week.