Security News

JetBrains urged customers today to patch their TeamCity On-Premises servers against a critical authentication bypass vulnerability that can let attackers take over vulnerable instances with admin privileges. Tracked as CVE-2024-23917, this critical severity flaw impacts all versions of TeamCity On-Premises from 2017.1 through 2023.11.2 and can be exploited in remote code execution attacks that don't require user interaction.

Exploit code is now available for a critical authentication bypass vulnerability in Fortra's GoAnywhere MFT software that allows attackers to create new admin users on unpatched instances via the administration portal. GoAnywhere MFT is a web-based managed file transfer tool that helps organizations transfer files securely with partners and keep audit logs of who accessed all shared files.

Fortra is warning of a new authentication bypass vulnerability impacting GoAnywhere MFT versions before 7.4.1 that allows an attacker to create a new admin user. GoAnywhere MFT is used by organizations worldwide to secure transfer files with customers and business partners.

Numerous Payoneer users in Argentina report waking up to find that their 2FA-protected accounts were hacked and funds stolen after receiving SMS OTP codes while they were sleeping. Starting last weekend, many Payoneer users in Argentina, whose accounts were protected by two-factor authentication, reported suddenly losing access to their accounts or simply logging in to empty wallets, losing "Years of work" worth in money ranging from $5,000 to $60,000.

CISA warns that a critical authentication bypass vulnerability in Ivanti's Endpoint Manager Mobile and MobileIron Core device management software is now under active exploitation. While it has yet to provide further details on CVE-2023-35082 active exploitation, CISA added the vulnerability to its Known Exploited Vulnerabilities Catalog based on evidence of active exploitation and says there's no evidence of abuse in ransomware attacks.
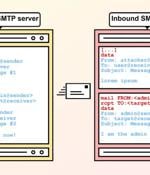
A new exploitation technique called Simple Mail Transfer Protocol (SMTP) smuggling can be weaponized by threat actors to send spoofed emails with fake sender addresses while bypassing security...

SE Labs advised CISOs to step-up their efforts against attacks on systems protected by MFA in response to increased attacker activity to exploit failure points. As is often the case when compromising systems, attackers have not reinvented the wheel to circumvent MFA, or 2FA, as it is also known.

A new phishing campaign pretending to be a 'copyright infringement' email attempts to steal the backup codes of Instagram users, allowing hackers to bypass the two-factor authentication configured on the account. When configuring two-factor authentication on Instagram, the site will also provide eight-digit backup codes that can be used to regain access to accounts if you cannot verify your account using 2FA. This could happen for multiple reasons, such as switching your mobile number, losing your phone, and losing access to your email account.

VMware has fixed a critical authentication bypass vulnerability in Cloud Director appliance deployments, a bug that was left unpatched for over two weeks since it was disclosed on November 14th. Cloud Director is a VMware platform that enables admins to manage data centers spread across multiple locations as Virtual Data Centers. "On an upgraded version of VMware Cloud Director Appliance 10.5, a malicious actor with network access to the appliance can bypass login restrictions when authenticating on port 22 or port 5480," VMware explains.

A new research has uncovered multiple vulnerabilities that could be exploited to bypass Windows Hello authentication on Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro X laptops....