Security News

ThreatFabric discovered a previous Anatsa campaign on Google Play in November 2021, when the trojan was installed over 300,000 times by impersonating PDF scanners, QR code scanners, Adobe Illustrator apps, and fitness tracker apps. In March 2023, after a six-month hiatus in malware distribution, the threat actors launched a new malvertizing campaign that leads prospective victims to download Anatsa dropper apps from Google Play.

He was the Gozi group's web expert, coding up bogus HTML content that the malware could inject into legitimate web pages in order to trick victims and steal their account information. Unlike many cybercriminals at the time, who profited from malware solely by using it to steal money, Kuzmin rented out Gozi to other criminals, pioneering the model of cybercriminals as service providers for other criminals.
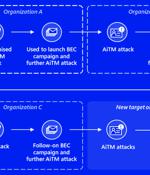
Banking and financial services organizations are the targets of a new multi-stage adversary-in-the-middle phishing and business email compromise attack, Microsoft has revealed. "The attack originated from a compromised trusted vendor and transitioned into a series of AiTM attacks and follow-on BEC activity spanning multiple organizations," the tech giant disclosed in a Thursday report.

Italian corporate banking clients are the target of an ongoing financial fraud campaign that has been leveraging a new web-inject toolkit called drIBAN since at least 2019. "The main goal of drIBAN fraud operations is to infect Windows workstations inside corporate environments trying to alter legitimate banking transfers performed by the victims by changing the beneficiary and transferring money to an illegitimate bank account," Cleafy researchers Federico Valentini and Alessandro Strino said.
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal. QBot is a banking trojan that's known to be active since at least 2007.
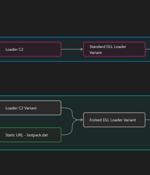
Multiple threat actors have been observed using two new variants of the IcedID malware in the wild with more limited functionality that removes functionality related to online banking fraud. "The well-known IcedID version consists of an initial loader which contacts a Loader server, downloads the standard DLL Loader, which then delivers the standard IcedID Bot," Proofpoint said in a new report published Monday.
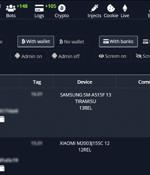
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud. "Nexus provides all the main features to perform ATO attacks against banking portals and cryptocurrency services, such as credentials stealing and SMS interception."
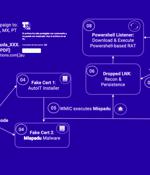
A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads. "One of their main strategies is to compromise legitimate websites, searching for vulnerable versions of WordPress, to turn them into their command-and-control server to spread malware from there, filtering out countries they do not wish to infect, dropping different type of malware based on the country being infected," researchers Fernando García and Dan Regalado said.

A new variant of the Android banking trojan named Xenomorph has surfaced in the wild, the latest findings from ThreatFabric reveal. "This new version of the malware adds many new capabilities to an already feature-rich Android banker, most notably the introduction of a very extensive runtime engine powered by Accessibility services, which is used by actors to implement a complete ATS framework," the Dutch security firm said in a report shared with The Hacker News.

A new Android banking trojan has set its eyes on Brazilian financial institutions to commit fraud by leveraging the PIX payments platform. "PixPirate belongs to the newest generation of Android banking trojan, as it can perform ATS, enabling attackers to automate the insertion of a malicious money transfer over the Instant Payment platform Pix, adopted by multiple Brazilian banks," researchers Francesco Iubatti and Alessandro Strino said.