Security News

A relatively new malware called Latrodectus is believed to be an evolution of the IcedID loader, seen in malicious email campaigns since November 2023. IcedID is a malware family first identified in 2017 that was originally classified as a modular banking trojan designed to steal financial information from infected computers.

A Ukrainian national has pleaded guilty in the U.S. to his role in two different malware schemes, Zeus and IcedID, between May 2009 and February 2021. Vyacheslav Igorevich Penchukov (aka...

Vyacheslav Igorevich Penchukov, 37, pleaded guilty to two counts related to his leadership role in both the Zeus and IcedID malware operations this week, netting millions of dollars in the process. Penchukov first became involved in the Zeus banking trojan as early as May 2009 but was only arrested over a decade later in Geneva, Switzerland in 2022.

Ukrainian national Vyacheslav Igorevich Penchukov, one of the heads of the notorious JabberZeus cybercrime gang, has pleaded guilty to charges related to his leadership roles in the Zeus and IcedID malware groups. The U.S. Department of Justice first charged him in 2012 for his involvement in the Zeus malware operation and the theft of millions of dollars using personal identification numbers, bank account numbers, credentials, and other sensitive info stolen from infected devices.

The threat actors linked to the malware loader known as IcedID have made updates to the BackConnect module that's used for post-compromise activity on hacked systems, new findings from Team Cymru reveal. "For the past several months, BackConnect traffic caused by IcedID was easy to detect because it occurred over TCP port 8080," Palo Alto Networks Unit 42 said in late May 2023.

Security researchers discovered a new malicious tool they named PindOS that delivers the Bumblebee and IcedID malware typically associated with ransomware attacks. PindOS is a simple JavaScript malware dropper that appears to be built specifically to fetch the next-stage payloads that deliver the attackers' final payload. Simple JavaScript malware dropper.
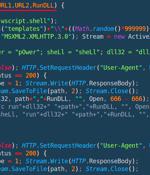
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID. Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its "User-Agent" string. Both Bumblebee and IcedID serve as loaders, acting as a vector for other malware on compromised hosts, including ransomware.
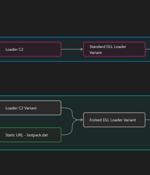
Multiple threat actors have been observed using two new variants of the IcedID malware in the wild with more limited functionality that removes functionality related to online banking fraud. "The well-known IcedID version consists of an initial loader which contacts a Loader server, downloads the standard DLL Loader, which then delivers the standard IcedID Bot," Proofpoint said in a new report published Monday.

New IcedID variants have been found without the usual online banking fraud functionality and instead focus on installing further malware on compromised systems. Proofpoint has identified two new variants of the IcedID loader, namely "Lite" and "Forked", both delivering the same IcedID bot with a more narrow-focused feature set.

A recent IcedID malware attack enabled the threat actor to compromise the Active Directory domain of an unnamed target less than 24 hours after gaining initial access. "Throughout the attack, the attacker followed a routine of recon commands, credential theft, lateral movement by abusing Windows protocols, and executing Cobalt Strike on the newly compromised host," Cybereason researchers said in a report published this week.