Security News > 2022 > January

RR Donnelly has confirmed that threat actors stole data in a December cyberattack, confirmed by BleepingComputer to be a Conti ransomware attack. While RRD initially said they were not aware of any client data stolen during the attack, on January 15th, the Conti ransomware gang claimed responsibility and began leaking 2.5GB of data allegedly stolen from RRD. However, a source told BleepingComputer that Conti soon removed the data from public view after RRD began further negotiations to prevent the release of data.

Organizations looking to minimize exposure to exploitable software should scan Twitter for mentions of security bugs as well as use the Common Vulnerability Scoring System or CVSS, Kenna Security argues. The initial Log4j vulnerability received a base CVSS score of 10.0.

Russia is positioned for a hot-war attack on Ukraine that the Biden administration warned could come "At any point" - but the country is already suffering an attack of a different kind. The perpetrators are taking pains to make the attacks look like a ransomware attack, even providing a ransom note.

An IRC bot strain programmed in GoLang is being used to launch distributed denial-of-service attacks targeting users in Korea. "Additionally, the DDoS malware was installed via downloader and UDP RAT was used."
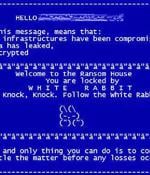
The financially motivated FIN8 actor, in all likelihood, has resurfaced with a never-before-seen ransomware strain called "White Rabbit" that was recently deployed against a local bank in the U.S. in December 2021. "One of the most notable aspects of White Rabbit's attack is how its payload binary requires a specific command-line password to decrypt its internal configuration and proceed with its ransomware routine," the researchers noted.

US companies should be on the lookout for security nasties from Ukrainian partners following the digital graffiti and malware attack launched against Ukraine by Belarus, the CISA has warned. "If working with Ukrainian organizations, take extra care to monitor, inspect, and isolate traffic from those organizations; closely review access controls for that traffic," added CISA, which also advised reviewing backups and disaster recovery drills.

The Cybersecurity and Infrastructure Security Agency urges U.S. organizations to strengthen their cybersecurity defenses against data-wiping attacks recently seen targeting Ukrainian government agencies and businesses.CISA is now urging business leaders and U.S. organizations to take the following steps to prevent similar destructive attacks on their networks.

Clearly, the stakes are high - gaining access to a Box account could give cyberattackers access to a vast array of sensitive documents and data for both individuals and organizations. When a user goes to log on with his or her credentials, Box generates the cookies and the user is asked to navigate to an SMS verification page, where the person is instructed to enter a one-time passcode sent to an enrolled mobile phone.

Toronto-based Citizen Lab has warned that an app required by Beijing law to attend the 2022 Olympics contains vulnerabilities that can leak calls and data to malicious users, as well as the potential to subject the user to scanning for censored keywords. The playbooks [PDF], which are documents that serve as info guides for Olympics-goers, instruct international visitors to download the app and use it to monitor health for 14 days prior to their departure for China.

UK's National Cyber Security Center has published new guidance for organizations to follow when communicating with customers via SMS or phone calls. Use a five-digit number instead of a regular phone number.