Security News

A recently disclosed security flaw in OSGeo GeoServer GeoTools has been exploited as part of multiple campaigns to deliver cryptocurrency miners, botnet malware such as Condi and JenX, and a known...

For the fourth time in the last five months, Apache OFBiz users have been advised to upgrade their installations to fix a critical flaw (CVE-2024-45195) that could lead to unauthenticated remote...

Apache has fixed a critical security vulnerability in its open-source OFBiz (Open For Business) software, which could allow attackers to execute arbitrary code on vulnerable Linux and Windows...

Cisco has fixed a command injection vulnerability in the Identity Services Engine (ISE) with public exploit code that lets attackers escalate privileges to root on vulnerable systems. [...]

Researchers have unearthed a cryptographic vulnerability in popular Yubico (FIDO) hardware security keys and modules that may allow attackers to clone the devices. But the news is not as...
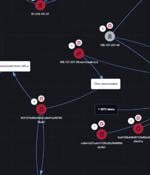
A hacktivist group known as Head Mare has been linked to cyber attacks that exclusively target organizations located in Russia and Belarus. "Head Mare uses more up-to-date methods for obtaining...

The world of cybersecurity is in a constant state of flux. New vulnerabilities emerge daily, and attackers are becoming more sophisticated. In this high-stakes game, security leaders need every...

Threat actors are actively exploiting a now-patched, critical security flaw impacting the Atlassian Confluence Data Center and Confluence Server to conduct illicit cryptocurrency mining on...

There are approximately 163 devices worldwide that are still exposed to attack via the CVE-2024-39717 vulnerability.

Fortra has addressed a critical security flaw impacting FileCatalyst Workflow that could be abused by a remote attacker to gain administrative access. The vulnerability, tracked as CVE-2024-6633,...