Security News

Apple on Thursday rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and the Safari web browser to address three new zero-day flaws that it said are being actively exploited in the wild. An anonymous researcher has been acknowledged for reporting the other two issues.
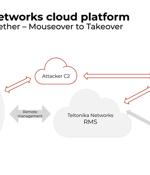
Several security vulnerabilities have been disclosed in cloud management platforms associated with three industrial cellular router vendors that could expose operational technology networks to external attacks. The 11 vulnerabilities allow "Remote code execution and full control over hundreds of thousands of devices and OT networks - in some cases, even those not actively configured to use the cloud."

Three new security flaws have been disclosed in Microsoft Azure API Management service that could be abused by malicious actors to gain access to sensitive information or backend services. This includes two server-side request forgery flaws and one instance of unrestricted file upload functionality in the API Management developer portal, according to Israeli cloud security firm Ermetic.

75% of organizations typically change or update their APIs on a daily or weekly basis, creating a significant challenge for protecting the changing API attack surface, according to Data Theorem and ESG. Insecure APIs plague organizations. In a related finding, study results also revealed the majority of organizations have experienced at least one security incident related to insecure APIs in the last 12 months, while the majority of organizations have experienced multiple security incidents related to insecure APIs during the past year.

CVE-2018-9995 is an authentication bypass vulnerability that can be triggered with a simple exploit sent via a maliciously crafted HTTP cookie to a vulnerable DVR device. The device responds by sending back the device's admin credentials in clear text.

Content delivery network and cloud services provider Akamai, which recently acquired API security firm Neosec in a deal expected to close in the next two weeks, is joining the API security ecosystem. Akamai noted companies use an average of 1,061 apps and, to give a sense of the scope of attacks, noted that there were 161 million API attacks on Oct. 8, 2022 and peaked on Oct. 9.

The U.S. Cybersecurity and Infrastructure Security Agency has added three flaws to the Known Exploited Vulnerabilities catalog, based on evidence of active exploitation. The second flaw to be added to the KEV catalog is CVE-2021-45046, a remote code execution affecting the Apache Log4j2 logging library that came to light in December 2021.

Overcoming industry obstacles for decentralized digital identitiesIn this Help Net Security interview, Eve Maler, CTO at ForgeRock, talks about how digital identities continue to play a critical role in how we access online services securely. PaperCut vulnerabilities leveraged by Clop, LockBit ransomware affiliatesClop and LockBit ransomware affiliates are behind the recent attacks exploiting vulnerabilities in PaperCut application servers, according to Microsoft and Trend Micro researchers.

Clop and LockBit ransomware affiliates are behind the recent attacks exploiting vulnerabilities in PaperCut application servers, according to Microsoft and Trend Micro researchers."Microsoft is attributing the recently reported attacks exploiting the CVE-2023-27350 and CVE-2023-27351 vulnerabilities in print management software PaperCut to deliver Clop ransomware to the threat actor tracked as Lace Tempest," Microsoft shared.

Hats off to PaperCut in this case, because the company really is trying to make sure that all its customers know about the importance of two vulnerabilities in its products that it patched last month, to the point that it's put a green-striped shield at the top of its main web page that says, "Urgent security message for all NG/MF customers." We've seen companies that have admitted to unpatched zero-day vulnerabilities and data breaches in a less obvious fashion than this, which is why we're saying "Good job" to the Papercut team for what cybersecurity jargon would probably praise with the orotund phrase an abundance of caution.