Security News

Critical security vulnerabilities in Cisco's Small Business RV Series routers could allow privilege escalation, remote code execution with root privileges on the devices and more. The critical bugs are part of 15 total vulnerabilities affecting the RV product line that Cisco disclosed this week.

Microsoft says Samsung devices enrolled in Microsoft Intune using a work profile will experience email and VPN connectivity issues due to missing certificates after upgrading to Android 12. Microsoft Intune is a cloud-based service designed to help admins manage Windows, macOS, iOS/iPadOS, and Android apps and devices in enterprise environments.

Myanmar's military junta has floated a cyber security law that would ban the use of virtual private networks, under penalty of imprisonment and/or fines, leaving digital rights organisations concerned about the effects of further closing the country off digitally to the outside world. As the country faced a military coup in February 2021, the newly installed Tatmadaw banned Facebook, Instagram, and Twitter, prompting users in the country to rely on VPNs to retain access to their preferred online communication services.
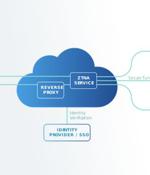
While VPNs are able to provide remote access, it may come as a surprise that they fall short when it comes to security. Many Lookout customers may have a similar experience that also includes accessing applications on AWS or Azure, such as SAP S/4HANA. As we work remotely, we've become accustomed to seamlessly accessing what we need wherever it is and to work from any device of our choosing.

Law enforcement authorities from 10 countries took down VPNLab.net, a VPN service provider used by ransomware operators and malware actors. The law operatives seized 15 servers used by the VPNLab.net service and took down its main site, so the platform is no longer available.

Microsoft has patched the patch that broke chunks of Windows and emitted fixes for a Patch Tuesday cock-up that left servers rebooting and VPNs disconnected. On the receiving end of the company's attention were Windows desktop and Windows Server installs left a little broken following Microsoft's latest demonstration of its legendary quality control.

VPNLab.net, a VPN provider that was used by malicious actors to deploy ransomware and facilitate other cybercrimes, was taken offline following a coordinated law enforcement operation. Europol said it took action against the misuse of the VPN service by grounding 15 of its servers on January 17 and rendering it inoperable as part of a disruptive action that took place across Germany, the Netherlands, Canada, the Czech Republic, France, Hungary, Latvia, Ukraine, the U.S., and the U.K. A second outcome of the seizure is that at least 100 businesses that have been identified as at risk of impending cyber attacks are being notified.

Microsoft has released emergency out-of-band updates to address multiple issues caused by Windows Updates issued during the January 2021 Patch Tuesday.All OOB updates released today are available for download on the Microsoft Update Catalog, and some of them can also be installed directly through Windows Update as optional updates.

Windows 10 users and administrators report problems making L2TP VPN connections after installing the recent Windows 10 KB5009543 and Windows 11 KB5009566 cumulative updates. These updates include KB5009566 for Windows 11 and KB5009543 for Windows 10 2004, 20H1, and 21H1. After installing yesterday's updates, Windows users find their L2TP VPN connections broken when attempting to connect using the Windows VPN client.

Technical details and exploitation notes have been published for a remote-code-execution vulnerability in Sonicwall SMA 100 series VPN appliances. This comes about a month after Sonicwall issued a patch for the security hole, which was discovered and privately disclosed by Rapid7's Jake Baines to Sonicwall in October.