Security News
An active malware campaign targeting Latin America is dispensing a new variant of a banking trojan called BBTok, particularly users in Brazil and Mexico. "The BBTok banker has a dedicated...
A new analysis of the Android banking trojan known as Hook has revealed that it's based on its predecessor called ERMAC. "The ERMAC source code was used as a base for Hook," NCC Group security researchers Joshua Kamp and Alberto Segura said in a technical analysis published last week. Regardless of these differences, both Hook and ERMAC can log keystrokes and abuse Android's accessibility services to conduct overlay attacks in order to display content on top of other apps and steal credentials from over 700 apps.
A new phishing attack likely targeting civil society groups in South Korea has led to the discovery of a novel remote access trojan called SuperBear. The intrusion singled out an unnamed activist, who was contacted in late August 2023 and received a malicious LNK file from an address impersonating a member of the organization, non-profit entity Interlabs said in a new report.

A previously undocumented Android banking trojan dubbed MMRat has been observed targeting mobile users in Southeast Asia since late June 2023 to remotely commandeer the devices and perform financial fraud. "The malware, named after its distinctive package name com.mm.user, can capture user input and screen content, and can also remotely control victim devices through various techniques, enabling its operators to carry out bank fraud on the victim's device," Trend Micro said.
A new remote access trojan called QwixxRAT is being advertised for sale by its threat actor through Telegram and Discord platforms. "Once installed on the victim's Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information," Uptycs said in a new report published today.

Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute Cloud (EC2) instances (virtual servers), as well as...
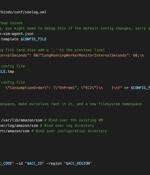
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services that allows the AWS Systems Manager Agent to be run as a remote access trojan on Windows and Linux environments. "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with SSM agent installed, to carry out malicious activities on an ongoing basis," Mitiga researchers Ariel Szarf and Or Aspir said in a report shared with The Hacker News.

Various European customers of different banks are being targeted by an Android banking trojan called SpyNote as part of an aggressive campaign detected in June and July 2023. What makes the malware strain notable is its dual functions as spyware and perform bank fraud.

Organizations in Italy are the target of a new phishing campaign that leverages a new strain of malware called WikiLoader with an ultimate aim to install a banking trojan, stealer, and spyware...
Threat actors are creating fake websites hosting trojanized software installers to trick unsuspecting users into downloading a downloader malware called Fruity with the goal of installing remote trojans tools like Remcos RAT. "Among the software in question are various instruments for fine-tuning CPUs, graphic cards, and BIOS; PC hardware-monitoring tools; and some other apps," cybersecurity vendor Doctor Web said in an analysis. "Such installers are used as a decoy and contain not only the software potential victims are interested in, but also the trojan itself with all its components."