Security News > 2023 > August > Researchers Uncover AWS SSM Agent Misuse as a Covert Remote Access Trojan
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services that allows the AWS Systems Manager Agent to be run as a remote access trojan on Windows and Linux environments.
"The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with SSM agent installed, to carry out malicious activities on an ongoing basis," Mitiga researchers Ariel Szarf and Or Aspir said in a report shared with The Hacker News.
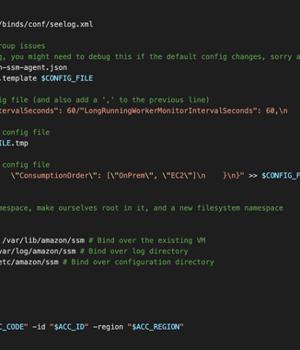
Specifically, it entails registering an SSM Agent to run in "Hybrid" mode, allowing it to communicate with different AWS accounts other than the original AWS account where the EC2 instance is hosted.
An alternative approach uses the Linux namespaces feature to launch a second SSM Agent process, which communicates with the attacker's AWS account, while the already running SSM agent continues to communicate with the original AWS account.
Last but not least, Mitiga found that the SSM proxy feature can be abused to route the SSM traffic to an attacker-controlled server, including a non-AWS account endpoint, thereby permitting the threat actor to control the SSM Agent without having to rely on AWS infrastructure.
"After controlling the SSM Agent, the attackers can carry out malicious activities, such as data theft, encrypting the filesystem, misusing endpoint resources for cryptocurrency mining and attempting to propagate to other endpoints within the network - all under the guise of using a legitimate software, the SSM Agent," the researchers said.
News URL
https://thehackernews.com/2023/08/researchers-uncover-aws-ssm-agent.html